Sign language communication across a volatile network.
Introduction
There are currently around nine million deaf or hard of hearing individuals in the UK, as specified by the Royal National Institute for the Deaf (RNID). Information services offered by the establishments are gradually improving, but still insufficient. In the UK, an estimated 70,000 deaf people use British Sign Language (BSL) as their first or preferred language [1]. However recognition of this fact is not reflected in the wider community in spite of the developments in broadcast and communications technology, leading to a marginalisation of sections of the deaf community, due to a language barrier.
There is also a chronic shortage of qualified BSL interpreters (1 per 275 users). Most major London Hospitals, for example, may take up to three weeks to arrange for a BSL interpreter for deaf patients, as opposed to offering interpretation services within twenty-four hours for over seventy international spoken languages.
The technological solutions for breaking down the language barrier do exist. For example, the RNID Text-phone [2], developed by the Information and Communication Theory Group, is based on a piece of software that provides a communication link between mobile phones (i.e. Nokia 9210) and land-based text-phones.
There is also VISICART, a European project aimed at developing computer based virtual signers for widening sign language support [3]. However the use of these systems, require specific hardware/software skills and devices, making the cost of wide-scale integration prohibitively high.
Systems such as TESSA and Simon the Signer that incorporate AVATAR modelling methods, tend to focus on the complete replication of a qualified interpreter, making the process both time consuming and costly [4]. However instead of using an AVATAR in its entirety, a visual language such as BSL can be communicated using several combined gestures, or from individual body parts such as the fingers, hands, lips, or the face.
This can be made even more effective by including additional parameters. For example, by mapping acoustic signals to facial animation parameters (FAPs), additional advantages especially with regard to narrow bandwidth recognition and conversion [5], has been particularly useful for those deaf individuals who are good lip-readers. This feature when combined with development in network capabilities, using algorithms such as the NTT Network Innovation Laboratories MaXimal Queuing (MXQ) system, is designed to provide optimal image transmission while minimising congestion.
This will enhance the transmission capabilities of multimedia applications that incorporate Virtual Reality (VR) data. The reverse process of sign language recognition for conversion to text is of particular relevance to many sign language projects. Methods employed in this domain, are unique and present additional design challenges such as co-articulation. Co-articulation relates to the connective gestures that need to be eliminated in order to preserve integrity of conversion [6].
The text conversion methods that are currently employed work well for a pre-programmed image library. However, they lack the flexibility required for continuous signed communication. The mapping techniques which these methods are based on tend to rely on captured image data specific to the application area. [7].
On the plus side for software developers in this field, studies have shown that image generators are now capable of offering refresh rates of 50fps [8]. In the past such processing rates were difficult to achieve but now are considered standard, making MPEG software demand for continuous sequential image transmission and rendering workable. Further development in areas such as data compression have offered additional flexibility in the design and adaptation of VR, with examples of files containing 29895 bytes, being reduced to 12996 bytes when combined with ASCII coded image elements [9].
Multiprotocol Label Switching (MPLS)
The rapid advancement in image data transmission techniques and current demand for faster and more efficient services, such as video conferencing, has left present day network service providers with a major problem. How can we deliver quality services at a cost effective price while maintaining existing services? Multiprotocol label switching (MPLS), [10] may well be the answer.
Most of us take for granted the services offered by many service providers when we purchase, for example, a new telephone or computer and wish to send an e-mail or text message. Our concern is not so much about how it works, just that it does work. The service providers, quite naturally on the other hand are concerned with maintaining current services, while looking to stay ahead of the competition by offering new and exciting products. With the subsequent increase in bandwidth and faster data transmission rates [11], this makes evaluation of network infrastructure and capabilities essential to ensure that not only can future public demands be met, but also that new and existing qualities of services are maintained [12].
MPLS appears to bridge the gap between the old services and existing methods of data transmission and the new consumer demand for higher speed data transmission and services. It is fast emerging as the industry standard with the ability to support higher-bandwidth transmission rates, cost effectively [13]. This technology is being closely monitored by all major network service suppliers, not only to take advantage of new capabilities but also to determine any potential problems. To invest in a technology which might prove incompatible or have a short shelf life, from a business perspective, could prove disastrous [14].
Troublesome Viruses
The Internet has enabled many people to start their businesses and is one of the great communication revolutions of the twentieth century; this technology has impacted most areas of the community, in e-commerce, education and advertising to name but a few. Its impact has been felt worldwide, but with this growth has followed some unwanted side effects, which are presenting difficulties for companies and establishments concerned about network security and management. One of the major causes of concern for network users and service providers is the computer virus [15].
The damage that a virus can do to a system by corrupting data and software is immense. This presents new challenges and concerns for service providers and users alike as the demand for the Internet increases. Many companies now perceive themselves to be at war against those who would deliberately write a virus aimed at malignant abuse of the network [16], and are employing various strategies to combat its growth. This is an ambitious task given the size and accessibility of the network structure.
In the past many hackers or virus writers were thought to be motivated by ego or intellectual challenge. However, there has been a rise in a new type of virus writer who is ideologically motivated. In one year there were a reported 5,589 such attacks on the UK alone.
Bandwidth Demand
Different services such as video and voice communication place different demands upon the network infrastructure. The figure below, figure 2, shows the situation from the mobile network service provider’s perspective. Video conferencing uses around four times as much bandwidth compared to voice communication. The high demands for additional video channels, in comparison to voice requirements over the mobile network, have had inevitable cost implications also.
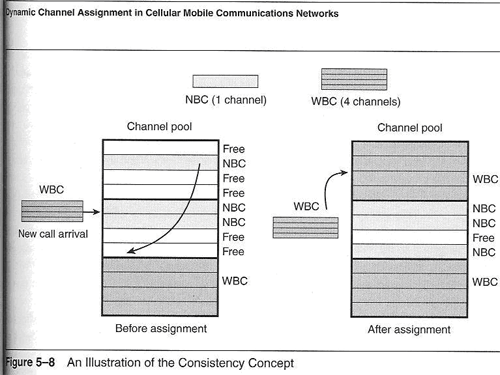
Figure 1 taken from Multimedia Application Support for Wireless ATM Networks p239
As can been seen from figure 1, before a call is made there exists a set number of available channels. However, after the service has been requested, in this case video conferencing, there are five available channels, shown as free. However, whereas these five channels could accommodate five narrow band calls (NBC), typically voice, four of the five are immediately taken for a conference call [17]. This is something referred to within the industry as video ‘hogging’.
Conclusion
There is no doubt that digital technology has had a positive impact on virtually every aspect of modern society. However, close attention needs to be paid to the negative impact also and the inherent or external threats that could undermine development. One such area of concern is the emergence of separate pricing packages for the video conferencing facility, which could impact on those in the deaf community who communicate through this service on a regular basis.
References
- RNID, 2004, Recognition of British and Irish Sign Language (BSL and ISL), Retrieved April 2011 from http://www.rnid.uk
- Action on Hearing Loss, 2011, Telecommunications, Retrieved June 2011 from http://www.actionforhearingloss.org.uk
- ViSiCAST, 2011, visicast-summary, Retrieved May 2011 from http://www.visicast.co.uk
- ViSiCAST, 2011, visicast-summary, Retrieved May 2011 from http://www.visicast.co.uk
- Petar S. Aleksic,. And Aggelos K. Katsagglos,. (2004) Speech-To-Video Synthesis Using MPEG-4 Compliant Visual Features, IEEE Transaction s on Circuit and Systems for Video Technology, Vol.14, NO.5 pp.682-691
- Pashaloudi N. Vassilia, Maggaritis G. Konstantinos,.(2003) Toward an Assistive Tool for Greek Sign Language Communication, The 3rd IEEE International Conference on Advanced Learning Technologies pp1-5
- JA Bangham, SJ Cox, M Lincoln, I Marshall, M Tutt and M Wells, (2000) Signing for the deaf using virtual humans, University of east Anglia and TeleVirtual. pp.1-4
- JA Bangham, SJ Cox, M Lincoln, I Marshall, M Tutt and M Wells, (2000) Signing for the deaf using virtual humans, University of east Anglia and TeleVirtual. pp.1-4
- Isenburg, M. and Snoeyink, J. (2002) Coding with ASCII: compact, yet text-based 3D content. Proceedings of the First International Symposium on 3D Data Processing Visualization and Transmission pp.1-7
- The International Engineering Consortium, 2011, Trillium-Multiprotocol Label Switching (MPLS), Retrieved January 2011 from http://www.binky-lights.org
- Cisco Systems White Paper, 1998, Alternatives for High Bandwidth Connection using Parallel T1/E1 Links, Retrieved March 2011 from http://www.cisco.com
- The International Engineering Consortium, 2011, Trillium-Multiprotocol Label Switching (MPLS), Retrieved January 2011 from http://www.binky-lights.org
- Piedad. F & Hawkins. M.,(2001) High Availability-Design, Techniques and Processes, Prentice Hall International (UK) Limited, p2
- Piedad. F & Hawkins. M.,(2001) High Availability-Design, Techniques and Processes, Prentice Hall International (UK) Limited, p4
- Stalling. W, (1999), Network Security Essentials-Applications and standards, Prentice Hall International (UK) Limited London, pp303-18
- Stalling. W, (1999), Network Security Essentials-Applications and standards, Prentice Hall International (UK) Limited London, pp303-18
- Rappaport. T.S., (2000), Multimedia Applications Support for Wireless ATM Networks, Prentice Hall (UK) Limited, pp238-40