The Current State of Cybersecurity Challenges in Modern Iot Devices
Introduction
This paper aims to examine the development of the phenomenon known as the Internet of Things (IoT). It attempts to highlight the potential cybersecurity challenges of IoT applications, and the related ethical issues that such cybersecurity challenges introduce. The essay is developed with the use of secondary data, particularly peer-reviewed journals, and reliable online sources. The essay concludes with an overview of the current innovative technological solutions that have been proposed as cybersecurity solutions for IoT devices.
The Internet of Things (IoT)
The Internet of Things (IoT) refers to a collection of interconnected devices through either wireless or wired Internet connection (Tawalbeh et al., 2020). Recently, IoT devices have become more popular and are widely adopted in various industries and home settings. Such devices are also used for industrial applications, such as transportation systems and power plants. Furthermore, current trends and projects, such as Industry 4.0, have aided in developing sophisticated business models and improving the interconnectivity between organisations’ systems (Sadeghi et al., 2015). A device within the IoT system could, therefore, include a car, electronic device, or various other systems (Abomhara and Koein, 2015). The communication between such devices is made through hardware elements such as sensors, mobile applications, and actuators, which enable the elements to interconnect with the digital world. Figure 1 below highlights the key elements of an IoT system.
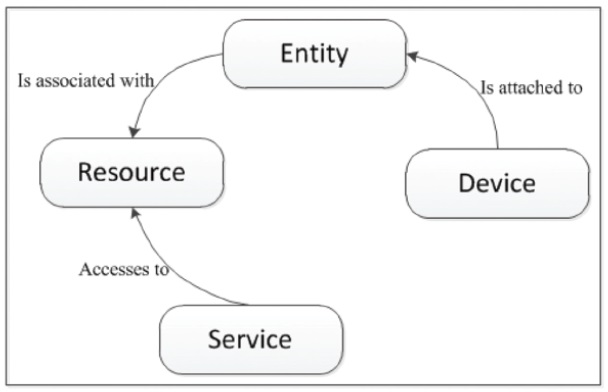
Figure 1: An example of an IoT System (Source: Abomhara and Koein, 2015)
Cybersecurity Challenges of IoT
The major diffusion of interconnected devices in an IoT system has increased the requirement for strong security measures in such systems. Particularly, IoT systems often amass a large volume of data, which is referred to as ‘Big Data’. Such data could include individuals’ and companies’ confidential information, and if accessed by unauthorised attackers, there could be major adverse impacts (Kumar and Patel, 2014).
Besides the increase in potential cyberattacks on IoT devices, there are also new and sophisticated tools accessible to attackers, which further improve the opportunities to gain unauthorised access to these devices. Thus, it is essential to investigate the potential cybersecurity solutions for IoT devices, to ensure that such devices can be successfully implemented and prevent vulnerabilities and threats. Some of the potential cyberattacks and vulnerabilities in IoT systems are further discussed in the next subsection.
1 Malware Injection
Malware refers to programming codes that are generated with the aim of conducting unauthorised or malicious activities (Karanja et al., 2017). IoT devices are susceptible to malware, which can be used by attackers to gain access to such devices or gain access to information stored on them. An example of the adverse impact of malware is the development of ransomware referred to as WannaCry, which was used for a cyberattack in 2017. The ransomware invaded various IoT devices in more than 100 countries and disrupted both corporate and government IoT networks and systems, which resulted in various negative outcomes (Brooks, 2021).
Other versions of malware programs, such as mirai and botnet have been developed for tailored cyberattacks on specific systems and networks. Such programs can also be used to identify default passwords on IoT devices, or access users’ systems remotely (Bertino and Islam, 2017). Malware programmers often design program obfuscation methods, such as metamorphism and polymorphism, which make it difficult to detect such attacks. Also, IoT devices are particularly more susceptible to these attacks because they are constantly connected to the Internet, unlike conventional standalone computer systems (Bertino and Islam, 2017).
2 Denial of Service Attacks
Denial of Service (DoS) attacks refer to cyberattacks whereby an attacker attempts to exhaustively consume all the available resources on a network. Thus, legitimate users are unable to gain access to such network or access information stored on their systems (Karanja et al., 2017). The Distributed Denial of Service (DDoS) is also like DoS, though this often includes a more coordinated attack, whereby an attacker attempts to use the resources of numerous network nodes. Both DoS and DDoS are major attack vectors for IoT systems, as attackers could gain access to such systems and flood them with various requests, thereby disabling services or slowing down the network’s performance.
3 SQL Injection Attacks
As previously mentioned, IoT technology is often used for various systems, including critical infrastructures, industrial control systems, and automated vehicles (Das and Gunduz, 2019). These systems store a huge volume of information in various databases, which could include confidential or corporate data. Therefore, IoT systems are highly vulnerable and could be targeted by attackers with the aim of stealing such information for nefarious purposes. An example of such attacks is SQL injection, which is aimed at stealing, modifying, or deleting the contents of a database (Das and Gunduz, 2019). To carry out a SQL injection attack, an attacker runs SQL query instructions that create access to the database of a system. This could result in major challenges for affected organisations or individuals, as stolen information could be used for malicious activities.
4 Advanced Persistent Threats (APTs)
Advanced Persistent Threat (APT) refers to a cyberattack whereby an attacker accesses a network and stays concealed for a while within the system. According to Das and Gunduz (2019), the major aim of an advanced persistent threat is to steal the information stored on networked systems. It often necessitates a multifaceted and advanced procedure and requires the use of sophisticated tools and methods. An example of an APT attack is the BlackEnergy attack, which is a Trojan that can be used to carry out both large-scale and small-scale DDoS attacks, cyber reconnaissance, and data theft. An example of such attack occurred in 2014, whereby a group of BlackEnergy attackers installed various SCADA-based plugins on their target’s Industrial Control Systems in various parts of the world (Kaspersky, 2021). This attack occurred over an extended period and was not easily detected. Such attacks can, therefore, have major consequences on the targeted organisations.
Ethical Issues related to IoT Security
Security and privacy concerns are considered some of the most significant ethical challenges related to the adoption of IoT devices. IoT devices are different from conventional systems, which make them more susceptible to cybersecurity challenges. For instance, various IoT devices are designed to be implemented on a large scale, such as sensors (Tawalbeh et al., 2020). Also, IoT often includes a collection of similar or almost similar devices that have identical features. The connection between the devices further magnifies the extent of any security vulnerabilities within the system.
This highlights the issue of privacy, as cyberattacks on IoT systems could result in the loss of users’ privacy. For instance, a system that stores users’ names, addresses, or credit card details could be targeted by attackers (Allhoff and Henschke, 2018). Subsequently, stolen information could be used for identity theft or fraudulent activities. Therefore, the use of IoT devices heightens the need for effective security measures, to ensure that users’ privacy is well-secured. There are also various privacy laws that are aimed at ensuring data owners’ privacy. For instance, regulations such as the Data Protection Act 2018 and Europe’s General Data Protection Regulation (GDPR) states that data users have certain privileges over their personal data. Examples of such privileges include the right to be informed about their data is being used and the right to data integrity and confidentiality (ICO, 2021). Therefore, organisations that collect private information should implement the suitable security measures so that such data is effectively secured. The lack of suitable security measures would, therefore, be considered non-compliance with certain regulations, such as the Data Protection Act.
Potential Security Solutions for IoT Security
Various studies on IoT security have proposed innovative solutions to the cybersecurity challenges related to IoT networks. Rashid et al. (2020) suggested the use of a machine learning-based anomaly detection system for IoT devices, particularly smart city applications. The authors suggest that the use of a machine learning algorithm would enable to the early detection of an attack on an IoT device or network. This is also applicable to cloud computing platforms, which are often used as storage devices for IoT applications. A training model can be implemented into network structures and cloud applications, with the ability to intelligently learn the normal activities on a network, and to detect any abnormal activities or anomalies. Similarly, Diro and Chilamkurti (2018) suggested a deep learning-based security infrastructure that can identify distributed attacks on an IoT system. The authors evaluated a deep learning model against a one-dimensional neural network and concluded that deep learning enables an intrusion detection system to learn a network’s behaviour and detect when it is being attacked.
On the other hand, in a study on IoT vulnerabilities, Dzaferovic et al. (2019) mentioned the use of a security infrastructure for IoT, which comprises of three major security factors, namely data, management and physical. The authors suggest that an information security infrastructure that considered these factors would create a three-dimensional data security system that would prevent a wide range of cyberattacks. Dao et al. (2017) also proposed a solution against DDoS attacks in IoT devices. Their solution is referred to as MECshield, which is a model that comprises of a fundamental controller and numerous agents positioned at the edge of every local network. Dao et al. (2017) suggest that such a network structure would effectively secure an IoT network against malicious network traffic.
Thus, it can be concluded that various security measures have been proposed in literature, Nonetheless, cybersecurity is an all-encompassing issue that requires further developments , as attackers constantly search for new and sophisticated methods for gaining unauthorised access to IoT systems and the information stored on such systems.
References
Abomhara, M. and Koien, G. M. (2015). Cyber Security and the Internet of Things: Vulnerabilities, Threats, Intruders and Attacks. Journal of Cyber Security, 4, pp. 65–88.
Allhoff, F. and Henschke, A. (2018). The Internet of Things: Foundational ethical issues. Internet of Things, 1-2, pp. 55-66.
Bertino, E. and Islam, N. (2017). Botnets and Internet of Things Security. Computer, 50, pp. 76-79.
Brooks, C. (2021). Cybersecurity Threats: The Daunting Challenge of Securing the Internet of Things. [Online]. Available at: https://www.forbes.com/sites/chuckbrooks/2021/02/07/cybersecurity-threats-the-daunting-challenge-of-securing-the-internet-of-things/?sh=4c00e9e05d50 [Accessed 27 August 2021].
Dao, N. et al. (2017). “Securing Heterogeneous IoT with Intelligent DDoS Attack Behaviour Learning. IEEE Communications Magazine.
Das, R. and Gunduz, M. Z. (2019). Analysis of cyber-attacks in IoT-based critical infrastructures. International Journal of Information Security, 8(4), pp. 122-133.
Diro, A.A. and Chilamkurti, N. (2018). Distributed attack detection scheme using deep learning approach for Internet of Things. Future Gener. Computing Systems, 82, pp. 761–768.
Dzaferovic, E., Sokol, A., Almisreb, A. A. and Norzeli, S. M. (2019). DoS and DDoS vulnerability of IoT: A review. Sustainable Engineering and Innovation, 1(1), pp. 43-48.
ICO (2021). Guide to the UK General Data Protection Regulation (UK GDPR). [Online]. Available at: https://ico.org.uk/for-organisations/guide-to-data-protection/guide-to-the-general-data-protection-regulation-gdpr/ [Accessed 27 August 2021].
Karanja, M., Masupe, M. and Jeffery, M. (2017). Internet of Things Malware: A Survey. International Journal of Computer Science & Engineering Survey, 8(3), pp. 1-20
Kaspersky (2021). BlackEnergy APT Attacks in Ukraine. [Online]. Available at: https://www.kaspersky.co.uk/resource-center/threats/blackenergy [Accessed 27 August 2021].
Kumar, J. S. and Patel, D. R. (2014). A survey on internet of things: Security and privacy issues. International Journal of Computer Applications, 90 (11), pp. 20–26.
Rashid, M. D. et al. (2020). Cyberattacks Detection in IoT-Based Smart City Applications Using Machine Learning Techniques. Int. J. Environ. Res. Public Health, 17, pp. 1-21.
Sadeghi, A. R., Wachsmann, C. and Waidner, M. (2015). Security and privacy challenges in industrial internet of things. In: Proceedings of the 2015 52nd ACM/EDAC/IEEE Design Automation Conference (DAC), San Francisco, CA, USA, 8–12 June, pp. 1–6.
Tawalbeh, L., Muheidat, F., Tawalbeh, M and Quwaider, M. (2020). IoT Privacy and Security: Challenges and Solutions. Appl. Science, 10, pp.1-17.