A Low Cost Solution for a Signature Capturing and Verification System using a webcam
Abstract
Signatures have been the most significant source of authorisation that has been used during the past few decades and it will remain the same for a very long time. The topic of signature verification was introduced to discourage the rise of signature forgeries in the present society. There are two types of signature verification, namely: Online verification and Offline verification. The author of this proposed signature verification solution is presenting this research report based on offline signature verification. This topic is a very widely discussed field at present and is a process used to verify whether a signature is genuine or forged. This Research Project contains information about a proposed solution called ‘SignPorte’ which means a barrier for signature forgeries. First, a database containing a large number of signatures is constructed. A scanned or a captured raster image of a signature is inserted and the system uses morphological filtering techniques to remove noise from the image. This is be followed by a thinning process. Next, the pre-processed image is subjected to feature extraction. The area and the angle of the signature are be obtained from the image. Feature extraction and the decision by neural networks will be the next few steps to be dealt with, before proceeding to the final decision of the signature generated by the system.
Introduction
A signature is considered to be a form of identification that has been used by almost all the human beings in this world. The significance of a signature is that it is unique to every person and cannot be forged with ease. It is a form of identification and adds a legal bearing to documents that have signatures on it. Hence it depicts the agreement of two people.
At present, we see so much crime taking place and we face huge risks in dealing with various routines in our day-to-day lives. Signature forgeries take place in almost all sectors in the industry and it is noted that banks are facing the highest fraud rate. Regarding bank cheque forgery, 40 percent of it is committed through signature forgery in the United States. The forgeries can be categorized into three different sections such as:
- Simple: Simple forgeries occur when the forger does not make any attempt to simulate or trace the original genuine signature (Zhou & Quek, 1996).
- Random: This type of forgery happens when the forger does not know the name or has not seen the signature before making a falsification.
- Skilled: Skilled forgeries occur when the forger practices to imitate the signature so that it is identical to the genuine signature and is very hard to recognize as a forgery (Zhou & Quek, 1996).
At present there are systems like PS-ASV (Progress Soft Automatic Signature Verification) and Parascript’s SignatureXpert. These systems use different approaches and techniques. What these do is that when a signature is scanned and processed for forgeries, they will match it with the reference signature that is available in the system. For scanning purposes, they use flatbed scanners. The author’s approach is to provide a low-cost solution using a web camera where the image processing would be difficult – that is, due to external factors like lighting in the environment etc. Also, because a scanner has a static environment for scanning where the lighting will be the same, compared to capturing using a web camera.
The approach that the author plans to use is that of a raster-to-vector conversion algorithm for image processing techniques to convert the signature image to an image of vectors. The advantage is that edge detection need not be used because the algorithm will find every edge and convert them into a vector image. After the image processing techniques like noise reduction, thinning and feature extraction are done, the system will use a trained artificial neural network algorithm for signature identification. (Katona et al., 1995)
Project Description
An Intelligent Low Cost Signature Capturing and Recognition System will capture the image of the signature using a web camera or a scanner. Then using Artificial Neural Networks it will be compared with the original source signature and recognize whether it is the original signature. Edge detection will be used in feature detection and feature extraction will be used to match the two signatures by means of special algorithms. Once the image is captured, it will be converted into a black and white image and then processed. This system needs to be trained very well in order to have better results. Signature(s) samples will be fed into the system for identification tests in order to maintain high accuracy in the system.
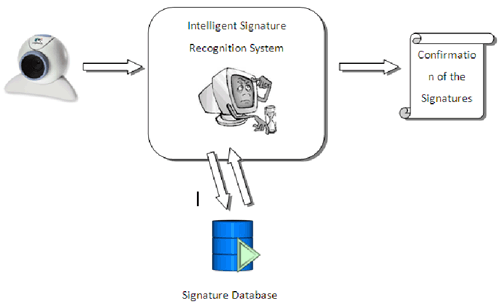
The database of this system can also be used by other parties because it is a signature database that will consist of thousands of customer details and their signatures.
Features of the Prototype
This section of the chapter contains the features of the prototype of the proposed solutions. The author describes each feature that should be included in the prototype.
- Signature Capturing
The prototype provides a user-friendly graphic user interface which can be operated to take images of the signature using a web camera or a scanner.
The speed of the retrieval process of the captured image is quite important because the solution is going to be used by banks which are very busy and almost always full. A delay in retrieval could reduce the number of daily transactions and hence be the system be shelved. - Signature Recognition
Once the image is fed into the system, the user will have to select the customer information and match the signature with image of the existing signature. This part of the process is the core feature of the system and needs to perform perfectly when being used for signature verification. The code needs to be written in such a way that it produces the most optimised performance. The manual process is very fast but there can be mistakes that happen from these counters due to the manual process. - Signature Database
A centralized database of correct signatures of the customers will be available. This particular database can be used by a lot of systems which require the customer information and their signature information.
Existing Applications
The research carried out shows what products are available in the market related to signature verification.
PS-ASV (ProgressSoft Automatic Signature Verification)
This is a system of which the prime objective is to reduce fraudulent cheques trying to invade payment methods. This is an intelligent system which can detect simple, random and skilled forgeries. This system detects the signature on the document and extracts the signature with powerful image processing techniques. The scanned signature image will be processed with several image enhancement techniques to come up with a clear and a better image for an accurate verification process.
The PS-ASV system is integrated with advanced technologies like artificial intelligence engines, analytical and geometrical analysis, and pattern recognition, to provide an automatic method to verify the enhanced image of the signature extracted from the cheque with the retrieved signature images. (ProgressSoft Corporation, n.d.)
Parascript SignatureXpert
The SignatureXpert application detects the presence of the signature, verifies signatures on cheques, Image Replacement Documents (IRD) and other documents. It is able to detect all types of forgeries such as random and skilled forgeries. This system applies a powerful combination of verifiers that include human-like, contextual signature interpretation; neural-networks-based learning and interpretation agents; fuzzy logic, and other advanced techniques. This system applies about seven verifiers to extract various features from the signature. (Parascript, LLC, 2000)
Therefore both of the above systems have already been implemented and are in use. However, the author is trying to implement an affordable, low-cost signature capturing and verification system with the use of a web cam. This will need a lot of image processing due to the use of a webcam.
Technical Approaches Available – Image Processing
Image processing is one of the main parts of signature verification especially in Offline Verification Systems where the signature image is captured using a flatbed scanner. If we consider an already captured signature image, quite a number of pre-processing needs to be done on that particular signature image. These are common pre-processing techniques used in signature verification systems. The author has conducted broad research and will explain each of these pre-processing techniques.
Grayscale
Grayscaling of images is one of the steps taken at the very beginning of the image processing cycle. The idea is to bring the RGB values of an image to the same intensity level. Calculation of an average grey colour is done by the separated RGB values that are acquired from a 3D array. The formula used to calculate the grey scale image is:
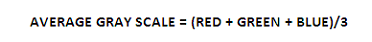
Once the above average is calculated, the value will be assigned as a new common value to each RGB component of each pixel. The output values are in the range within 0 – 255. If the value exceeds the boundary, it will be set to the boundary values. E.g.: any value that includes 255 will be set to 255 and similarly with 0.
The reason for converting to a greyscale image is to bring a low profile or less information to each pixel. The idea behind it is that grey is the only colour containing the same intensity levels of RGB. Converting to greyscale will always help the image processing because most of the subtle details are highly visible in the grey level.
Background Removal
Background removal is a very important pre-processing technique in pattern matching or pattern recognition since it is noted that an image with a clear background is required. Also, data areas should be cropped before extracting features. Several thresholding methods are being used for this purpose like P-Tile thresholding.
This step will be used to remove disturbances like printed text on the document. Therefore removal of the background is necessary to identify the image and the needed sections on the image. Not using this step will always result in the incorrect output; for an application like signature verification it is crucial to capture the proper data areas of a signature image.
Noise Reduction
The main reason for the use of noise reduction technique is to remove all sorts of disturbances in the image. Essentially, there will be a large amount of dirt and dust on cameras and scanners, while imperfections in scanner lighting etc., can introduce various noises in images. In the filtering process, morphological filtering techniques will be followed. In this method, the image repeatedly goes through an erosion process followed by a dilation process.
Thinning
The main idea of thinning is to reduce the thickness of the image, especially the pen strokes. Thinning is done by reducing the thickness into one pixel. The research looks to using a morphological thinning for this purpose. The image will be thinned an infinite number of times until the image reaches the maximum thinning where there is no difference in the thickness of the signature in an image.
Feature Extraction
Feature extraction is an important stage where the features of each signature are captured. The idea of this step is to identify each and every minor detail of a signature. A signature contains highly intrapersonal skills that vary from person to person. Subsequently identifying the features and extracting them properly will lead to a better or more accurate verification. Some of the features that need to be extracted are:
- Width and height of the rectangular space where the signature is laid
- Nodes and edges in the graph
- Histogram containing the edge direction and length
Edge Detection
The idea of edge detection is to provide high details on edges. An edge is a boundary of certain object or two different regions. Gonzalez and Woods (2000) state that edge detection is known to be the most used approach for identifying various abnormalities in grey level. A Laplacian algorithm is one of the most well-known algorithms used for edge detection.
The author will not be using edge detection in this project because the use of raster-to-vector conversion will help the author find all the points available in the image resulting in a representation of a vector graph.
AI – Artificial Intelligence
Artificial intelligence has been one of the most popular topics in the field of Information and Communication Technology and it is being very widely used in high-end applications. AI was introduced in the 1950s and since then there have been various developments and new models of intelligence related to natural intelligence. Some of the key developments in the field are:
- Artificial Neural Networks
- Genetic Algorithms
- Case Based Reasoning
- Fuzzy Logic
The author will explain each of the above mentioned models in detail.
Artificial Neural Networks
A neural network is a parallel distributed processor that has a natural propensity for storing experiential knowledge and making it available for use. It resembles the brain in two respects (Haykin, 1998).
It represents a model of parallel processing which has been inspired by the human brain. It is also called an emulation of a biological neural system. Artificial Neural Networks also have special features like supervised/unsupervised learning, self-organization and Real Time Operation.
Advantages of Artificial Neural Networks (ANN)
- A neural network can perform tasks that a linear program cannot.
- When an element of the neural network fails, it can continue without any problem because of its parallel nature.
- A neural network learns and does not need to be reprogrammed.
- It can be implemented in any application.
- It can be implemented without any problem.
Disadvantages
- The neural network needs training to operate.
- The architecture of a neural network is different from the architecture of microprocessors therefore needs to be emulated.
- It requires a high processing time for large neural networks.
The researcher considers that the use of ANN will help signature verification because ANN will be helpful to measure the threshold of acceptance of a signature once it is trained for signature samples. Feeding proper information will always help the system to make decisions at a higher expertise level hence, the experts say that ANN information driven rather than being driven by data. Also considering the disadvantages such as requiring a high processing time will not affect this system since this system will not be a large system.
Genetic Algorithms
These are general search methods. Genetic algorithms use analogies from natural selection and evolution. When a specific problem is given these algorithms, it will encode a particular potential solution using a simple string of alphabets, called a chromosome and will apply operators of reproduction and recombination to create new chromosomes (Russel & Novig, 1995). These algorithms include various features like
- Function optimization
- Problem solving
- Machine learning
Fuzzy Logic
“Fuzzy logic was developed by Zadeh in the mid 1960s for representing uncertain and imprecise knowledge” according to (Jain & Martin, 1998)
Fuzzy logic takes a complex sentence such as TallPerson(Nate) V Smart(Nate) and determines its truth value as a function of the truth values of its components (Russel & Novig, 1995). Fuzzy logic can handle a situation when there is more than one possible solution to a given problem.
Integrated Neural Classifiers
This is another approach available when using neural networks. This approach speaks about two neural classifiers which are:
- Base Classifier: Base Classifier can be used to measure a threshold of certain patterns by looking at the distance variation. So, a comparison of two signatures made by the same person will not have much of a deviation than if one of the signatures was from an impersonator copying it.
- Integrated Classifier: Contains two sub parts – Parallel and Sequential. Since neural networks have several layers, the second layer of the parallel model will obtain results of the first layer as its input. Lack of direct knowledge of the sample distribution is the main defect in this module (Liang et al., n.d.).
Support Vector Machine (SVM)
SVM is a new learning method which was introduced by V. Vapnik. SVM is also called as very universal learners. This methodology makes sure that there will be a very small percentage of misclassification errors of data both in the training set and test set. With a set of examples from two classes, a SVM finds the hyper plane, which maximizes the distance from either class to the hyper plane and separates the largest possible number of points belonging to the same class on the same side (Özgündüz et al., n.d.)
Hidden Markov Model
This model is mostly used in the field of pattern recognition like handwriting verification and also speech recognition etc. These stochastic (random) models are such that they can absorb subtle variability between patterns and their similarities.
Limitations of the Solution
- The system has been only trained for two signatures and prior to deployment of the system it needs to be trained accordingly to the relevant signature training set and mapped to the correct result set.
- The system is only designed for simple forgeries. A person imitates another person’s signature without knowing what the original signature looks like.
- The system does not provide any graphical representation of data to evaluate the acceptance and rejection rate of signatures.
- The author has only created a simple graphical user interface, yet has made it more interactive and easy to use. Since this is a banking application, the author has designed the GUI in such a way that the users of the system can always perform the core functionalities within the frame of one graphical user interface.
- The system does not use a centralized database to store the signatures. The author has to maintain a large database of testing data so, therefore, a dataset of 69 signatures has been used for testing. The author is looking forward to expanding the training dataset.
Future Enhancements
- Graphical User Interface
The graphical user interface needs to be designed to be much more appealing to the stakeholders. The prototype has been developed only to suit the core functionality of the system. - Feature Extraction
The author would like to extract more features from each signature in order to identify the best matching signature. The extraction of proper features will always tell on the accuracy of the final result provided by the system. Certain systems use several extraction methodologies in order to obtain a maximum number of features. This can be as many as thirty to forty signature features. - Use Of A Centralized Database
This solution can be enhanced in such a way to have a centralized database so that any bank branch can connect and retrieve the relevant signatures from the system to compare with the signatures on the document. - Further Training
The author considers that training this system with more and more signature samples would always result in the types of solutions where the ANN used can yield even better results.
Conclusion
This research paper has identified highly technical aspects of verifying genuine signatures. It also has covered the various types of image processing techniques that have been used in order to pre-process an image prior to subjecting for verification. The image processing techniques mentioned here are the basic pre-processing techniques that need to be used in order to prepare the image by converting it in to grayscale, for the reduction of noise in the image.
The study on Artificial Neural Networks has indicated the various types of Artificial Intelligence techniques that can be used in order to obtain the final result of the solution. The author suggests the use of ANN with a back propagation algorithm which has its own unique learning style.
In conclusion, the paper contains ideas for the implementing a low cost signature verification solution for signature images captured using a web camera which significantly reduces the time that is taken by a flatbed scanner to scan a signature image for verification.
Bibliography
Gonzalez, R.C. & Woods, R.E., 2000. Digital Image Processing. 5th ed. Singapore: Addison Wesley Longman.
Haykin, S., 1998. Feedforward Neural Networks: An Introduction.
Jain, L.C. & Martin, N., 1998. Fusion of Neural Networks, Fuzzy Systems and Genetic Algorithms: Industrial Applications. Adelaide.
Katona, E., Palágyi, K. & Tóth, N., 1995. Signature verification using neural nets. In Proceedings of the Scandinavian Conference on Image Analysis. Scandinavia, 1995.
Letric Law Library, n.d. FORGERY. [Online] Available at: HYPERLINK “http://www.lectlaw.com/def/f056.htm” http://www.lectlaw.com/def/f056.htm [Accessed 25 November 2009].
Liang, W., Zhouchen, L. & Rongchun, Z., n.d. Signature Verification using Integrated Classifiers.
Mahar, J.A., Khan, M.K. & Mahar, P.D.M.H., 2007. Off-Line Signature Verification of Bank Cheque Having Different Background Colours. IEEE, pp.738-45.
Özgündüz, E., Şentürk, T. & Karslıgil, M.E., n.d. OFF-LINE SIGNATURE VERIFICATION AND RECOGNITION BY SUPPORT VECTOR MACHINE. p.4.
Papunzarkos, N. & Baltzakis, H., 1997. OFF-LINE SIGNATURE VERIFICATION USING MULTIPLE NEURAL NETWORK CLASSIFICATION STRUCTURES., 2-4 July 1997.
Parascript , LLC, n.d. Parascript SignatureXpert. [Online] Available at: HYPERLINK “http://www.parascript.com/products2/SignatureXpert_brochure.pdf” http://www.parascript.com/products2/SignatureXpert_brochure.pdf [Accessed 3 November 2009].
Parascript Corporation, 2007. A State-of-the-Art Solution for Off-Line Signature Verification. Parascript SignatureXpert, p.11.
Parascript, LLC, 2000. Parascript SignatureXpert. Parascript, p.2.
ProgressSoft Corporation, n.d. About Us: ProgressSoft Corporation. [Online] Available at: HYPERLINK “http://www.progressoft.com/?option=com_products&act=content&id=11” http://www.progressoft.com/?option=com_products&act=content&id=11 [Accessed 3 November 2009].
Russel, S.J. & Novig, P., 1995. Artificial Intelligence: A Modern Approach. New Jersey: Alan Apt.
Zhou, R.W. & Quek, C., 1996. An Automatic Fuzzy Neural Network Driven Signature Verification System. 2, pp.1034 – 1039.
Anon., 2004. Offline signature verification using the discrete radon transform and a hidden Markov model. ACM Portal, 2004(ISSN:1110-8657), pp.559-71.
Bansal, A., Garg, D. & Gupta, A., 2008. A Pattern Matching Classifier for Offline Signature Verification. (ISBN:978-0-7695-3267-7 ), pp.1160-1163.
Bhole, D.K. & Velankar, S., 2010. Comparison of offline signature verification using graph matching based approach and cross validation approach. ACM Portal, N/A(ISBN:978-1-60558-812-4), pp.672 – 673.
Bonilla, J.F.V., Ballester, M.A.F., Gonzalez, C.M.T. & Hernandez, J.B.A., 2009. Offline Signature Verification Based on Pseudo-Cepstral Coefficients. ACM Portal, N/A(ISBN), pp.126 -130.
Ruiz-Del-Solar, J., Devia, C., Loncomilla, P. & Concha, F., 2008. Offline Signature Verification Using Local Interest Points and Descriptors. ACM Portal, (ISBN:978-3-540-85919-2 ), pp.22