Essay on Data Security
Number of words: 1346
Database security procedures differ slightly from internet security techniques. The former entails architectural steps, software applications, and even staff education. However, it is also critical to safeguard the site to reduce the possible cyber threats that cyber attackers may use (Kaila & Nyman, 2018). The following are some strategic and technological database security methods that might assist organizations in protecting their sensitive data.
Deploying physical database security
Foreign people or even internal threats might cause physical attacks on data centers or systems. If a cybercriminal gains tangible database system access, they can take the data, damage it, or even implant harmful software to obtain remote access. Because these sorts of assaults may circumvent digital security standards, they are frequently hard to discover without extra protection precautions. When selecting a web hosting provider, the firm should look for a proven track record of handling security seriously. It is also advisable to minimize free hosting providers due to the potential for security breaches. If one is hosting their servers, basic security procedures such as cameras, passwords, and operated security people are strongly advised (Lal et al., 2017). Additionally, any practical server accessibility should be documented and restricted to specific individuals to reduce the possibility of malicious activity.
Separating Database Servers
Databases involve particular security procedures to protect them against attackers. Moreover, storing the data on the same platform as the website subjects it to other threat avenues that strike websites. Assume a firm operates an online marketplace and keeps its website, non-sensitive data, and confidential data on the very same server. To safeguard against intrusions and fraudsters, they can utilize the host agency’s website security protocols and the eCommerce system’s security capabilities. However, the confidential data is now exposed to attackers via the website and the online shop network. An attacker who penetrates either the website or the online shop platform can get the databases as well. To reduce these concerns, the firm should keep the data structures isolated from the rest of the infrastructure (Williams, 2015). They should also utilize real-time safety data and tracking systems devoted to databases protection and enable businesses to take rapid action in the case of an intentional intrusion.
Setting up a proxy server
Before contacting the data warehouse, an HTTP proxy examines requests received from a workstation. In some ways, this server serves as a firewall, attempting to keep unauthorized queries out. HTTP is the most often used protocol for proxy servers. If the firm is working with confidential information, such as credentials, payment details, or personal details, an HTTPS server should be set up (Kaila & Nyman, 2018). In this manner, the data passing via the proxy server is likewise encoded, adding an extra degree of protection.
Avoid Using default network ports
When data is sent across servers, the TCP and UDP technologies are utilized. When such interfaces are configured, they use the standard network ports. Because of their prevalence, standard ports are frequently exploited in brute-force cyberattacks. When not using the standard ports, the cybercriminal that targets the corporate server must use trial and error to test other port number variants. Because of the increased labor required, the attacker may be discouraged from continuing their attack efforts (Lal et al., 2017). However, before allocating a new port, the firm should verify the Internet Method Of analyzing the Authority’s port register to guarantee that the new route isn’t already in use by another service.
Use real-time database monitoring
Actively monitoring the database for attempted breaches strengthens security and helps one to respond to future threats. The organization may use tracking software to log all operations performed on the database’s infrastructure and notify them of every intrusion. Moreover, they should establish escalation processes in the event of a suspected attack to keep critical data considerably safer. A further factor to address is frequent audits of security issues and performing security penetration tests (Williams, 2015). These enable the firm to identify any security flaws and repair them before a possible breach occurs.
Deploy data encryption protocols and use application firewalls
Encrypting data is vital for protecting proprietary information and transferring or storing confidential user information. Putting in place data protection techniques reduces the chances of a constructive data breach. This implies that even if thieves get access to the data, the information will stay secure. Firewalls are the initial line of defense against unauthorized access. In addition to securing the site, one should deploy a firewall to secure their database from several vulnerabilities. The organization should ensure that the firewall is appropriately configured to address any security gaps (Kaila & Nyman, 2018). It is also critical to maintaining the firewalls up to date since this safeguards the site and database against new attacker tactics.
Creating regular backups
While it is usual to make backups of the websites, it is critical to back up the databases continuously. This reduces the danger of losing crucial material as a result of malicious assaults or malicious attacks. Windows and Linux should be used to generate backups of data on the most common servers. In addition, to improve security, the firm should guarantee that the backup is kept and protected on a different server (Williams, 2015). In this manner, the data is retrieved and secure even if the central database server is hacked or stays unreachable.
Use strong user authentication
Passwords have been hacked into user accounts in about 80% of security breaches cases. This demonstrates that passwords solely aren’t a suitable security mechanism, owing to the human-error component in generating secure passwords. To address this vulnerability and provide an additional layer of protection to the database, the firm should use a multi-factor verification procedure. Even if identities are hacked, cyber thieves will struggle to circumvent this security system. To further reduce the danger of a possible breach, they should only allow verified IP addresses to enter the database (Williams, 2015). While IP addresses may be duplicated or disguised, it takes more work on the attacker’s part.
Security Model To Develop Databases For Organizational Security
By basing security procedures on excellently identified and often policy security models, the system will evolve and eliminate shortcomings in the process. The business should consider which structure is best for them and whether sector rules outline a specific strategy that the security plan must adhere to. CIS 20 is one of the most widely used core cybersecurity models that businesses worldwide use to achieve a high degree of program development. The CIS 20 is a set of controls developed by the Centers for Cybersecurity in response to a security breach united states military sector in 2008. A series of measures are judged necessary to protect an organization’s system from large-scale cybersecurity threats (Matulevičius & Lakk, 2015). The CIS 20 is divided into three major control categories:
- Controls Fundamentals (like inventory control, continuous vulnerability management, and controlled employee privileges)
- Controls that are fundamental (like malware defenses, data protection, or wireless access controls)
- Controls in Organizations (include training programs and creation of incident response teams).
The CIS 20 cybersecurity model is intended to be comprehensive, requiring considerable concentration and care in a company’s security governance process (Radziwill & Benton, 2017). The diagram below shows a security model and how it flows to ensure the database is secure.
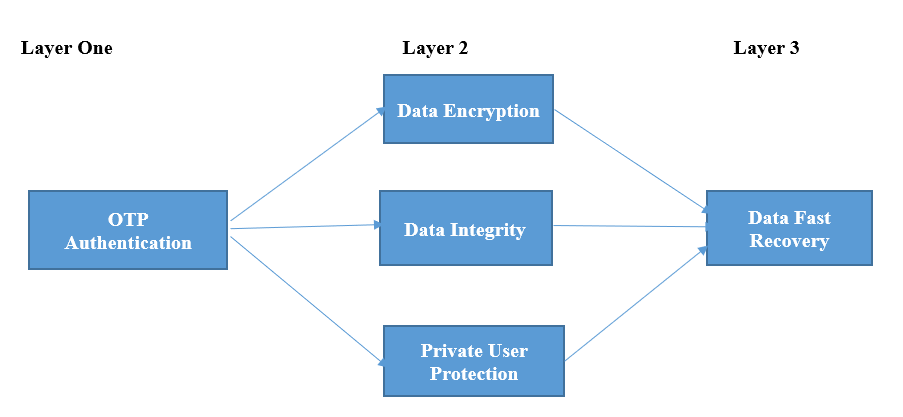
References
Kaila, U., & Nyman, L. (2018). Information Security Best Practices. Technology Innovation Management Review.
Lal, S., Taleb, T., & Dutta, A. (2017). NFV: Security threats and best practices. IEEE Communications Magazine, 55(8), 211-217.
Williams, T. D. (2015). The Value of Threat Models in Enterprise Security Testing of Database Systems & Services.
Matulevičius, R., & Lakk, H. (2015). Model-driven role-based access control for SQL databases. Complex Systems Informatics and Modeling Quarterly, (3), 35-62.
Radziwill, N. M., & Benton, M. C. (2017). Cybersecurity cost of quality: Managing the costs of cybersecurity risk management—arXiv preprint arXiv:1707.02653.