Essay on Site Precious Hospital Challenges and Implementation
Number of words: 3145
Precious Hospital is attracted in an elevation to its organization network framework. Employees have complained about slow response time when accessing the network during peak time. At the very least, Precious Hospital desires to address these matters through advancement to its framework. Yet, the board is additionally appearing to have the option to rally efficiency and improve personal data security in their organization.
The projected plan includes critical deviations to Precious Hospital network frameworks. The existing apparatus utilized throughout the organization network was purchased significantly and used a wide array of advancements. The new essential network topology design will entail a few redesigns in equipment used (contrary qualities and seasoned improvements). The outcome will be improved speeds, more first-rate dependability, and more straightforward upkeep of organization parts. The renovated equipment will use something like a date, viable developments that will significantly boost inspecting and upkeep just as resolute the sluggish admittance times that are presently being reported, notwithstanding refreshing the equipment, the proposed arrangement diagrams a few changes in the organization setup. These variations, whenever implemented, will give reliable security and quality to all patrons of the Precious Hospital network. With the new equipment, the new network design will open the door for Precious Hospital to inspect other opportunities in utilizing the web to build in general productivity and, ultimately, improved service to their patients’. The arrangement illustrated underneath will give the best advantage conceivable to Precious Hospital – – meeting the entirety of their current needs and accommodating future extension – at the least expense possible. The task’s final assessed cost is shy of $850,000; this considers settling current organization issues, yet besides the general expense of organization possession.
| Points of failure | Solutions |
| Respectively, a server holds patients. Switch laying-off: if problems in a network occur owing to switch X failure, switch Y still should be functional and provide the links to the server, to the other remaining dispersal switches, and the WAN connection. This laying-off result will thwart the system of the network down since it is utilizing a single switch. | Occasionally computer users unintentionally harm data, hardware, applications, or even software configurations. The Precious Hospital network manager should take cautionary actions and take note of systems and networks to ensure nothing suspicious occurs. e.g.: · Any possible laying-off should be dealt with to protect the network system availability. With redundant wiring, fail-over capabilities in the switches, and NICs in the server that those computer units use. These technologies link to a backup in UPS for the servers that holds patient data and unified records backup for every server. · Link laying-off: in case of a link failure, provide a backup to the server. |
In rundown, the essential objective of this venture is to update the current network of Precious Hospital. The aim will be to overhaul the emergency clinic WAN and the LAN connections redesign, forming a disengaged VLAN for the Medical hospital patients and guests’ unrivaled firewall security. Our overhaul suggestion, incorporating the physical and consistent plan and details for the organization, appears on an outline, including these alterations. A security evaluation achieved the organization’s security, fused toward the foundation of another Precious Hospital network security strategy that considers the organization overhaul, and observed HIPAA guidelines. The gauge for the organization’s usage overhauls per suggestion will bring about an expense of under 900,000 dollars to Precious Hospital. Our conviction, with the new organization overhauls, Precious Hospital will accomplish its objective of modernizing its mechanical assets. Likewise, the recent organization redesigns’ execution will give the primary and much-required advantage of improving Precious Hospital adaptation to non-critical failure and security, just as provide a fast association.
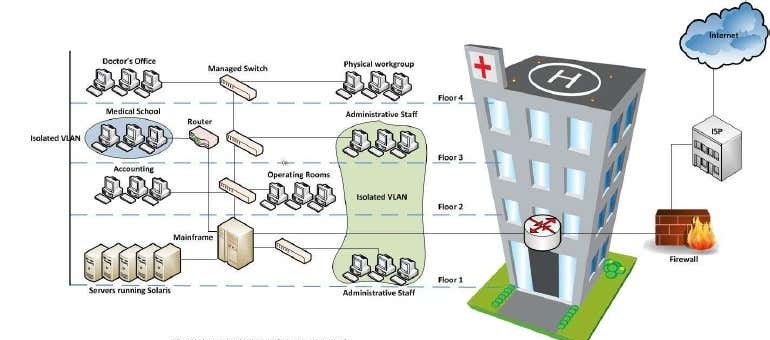
Figure 1 precious Hospital Topology
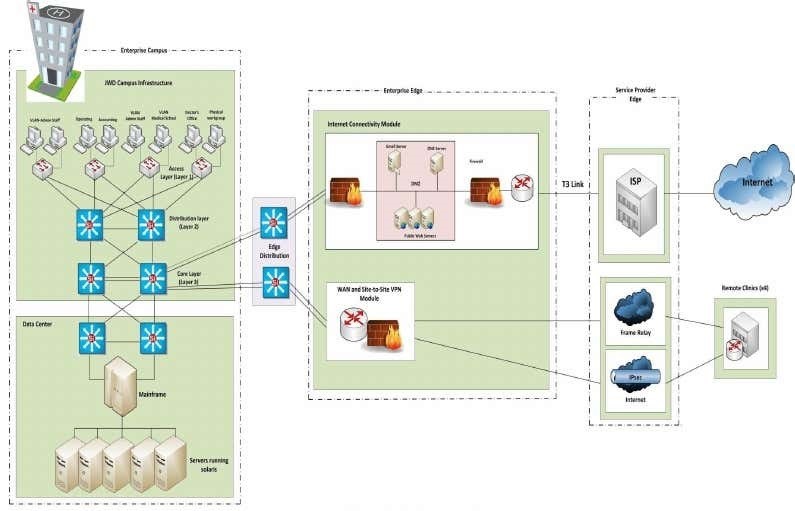
Figure 2 precious Hospital network design
Site Beast College- School of Informatics
Site Details and Challenges
This report plans to cover a network establishment for another three-floor building at Best College – School of Informatics. The fundamental arrangement includes a LAN plan that will endure for the following five to seven years; however, it can likewise give way to any future redesigns. The organization’s equipment will comprise various devoted servers and will also deliver catalog administrations and database administrations. The Localized Area Network will be versatile and protected, with the capacity to deal with great traffic loads and maintenance video and voice services. Additionally, it will be perceptive and improvable to provide for additional clients. The school comprises four offices: general administrative and staff, where every individual from the two divisions will have their PC connected with a printer and a server. However, the administrative staff will utilize a typical printer; The technical staff, where the entirety of its individuals will have their PC and access to all networks and all organizations, yet admittance to all storerooms. And secure storeroom.
Solution(s)
The current design, a two-level fell center progressive organization model. It is proposed because it offers similar advantages as a three-level plan, which encourages adaptability and separation through subnetting, improving flexibility, and diminishing expense. It gives the elements of the center and conveyance layer in a single gadget.
The complete network uses both wired and wireless connectivity. Wireless connectivity is not recommended due to its disadvantages, such as slower speeds due to signals being blocked by walls and other physical features (Simons, 2019). To keep an organized and well-planned cabling network at the central distribution core, the network follows a typical structural cabling typical, such as the EIA/TIA-568, which recommends colored cables with proper labeling and patch panels easy managing. The lines foldaway from rack to rack via upstairs cable pathways. With horizontal and vertical cable use, managers at the racks’ sides end up to their corresponding device while keeping an organized cabling environment. These designed approach proposals are scalable, reliable, and practicable cabling setup (Chan, 2019).
The type of cables used for the network will be based on which gadgets existing in the model. The table beneath explains the different wires (Partsenidis, 2017).
| Cable
| Distance | Data Rate | Application |
| Fiber Optic | 40 KM | Max 10Gbps | 10-gigabit ethernet Large enterprises- industrial |
| CAT7 | 200 meters | 10gbps max | 10Gigabit Ethernet Backbone -large- sized campuses |
| CAT6 | 100 meters | Max 10gbps | 10Gigabit Ethernet Backbone – medium- sized campuses |
| CAT5e | 50 meters | Max 1Gbps | Fast Ethernet( Hosts gadgets) |
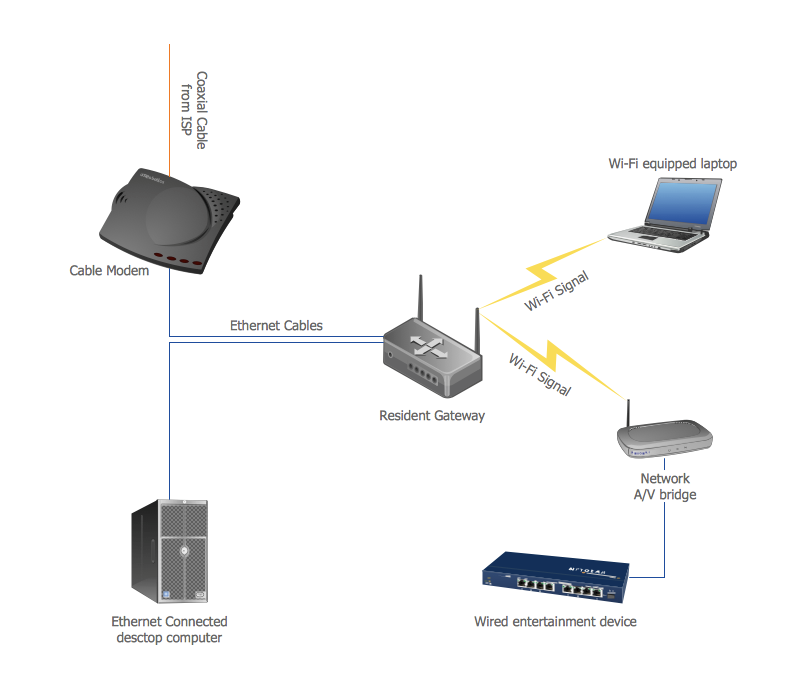
Figure 3 Physical topography diagram
Gadget Placement and Selection
The gadgets are selected based on a hierarchical prototype that is going to be executed. A router functions as the default entryway at the center and directs the traffic outside and inside the network. At this time, traffic is controlled by a firewall due to security reasons, as shown below. The picked switches are the most ideal for this arrangement since they offer full design highlights. For example, assurance over DDNS assaults, Quality of Service, and the capacity to make Virtual LANs (VLANs); however, they are likewise stackable. They could be various switches operating as one. Elective choices were the particular switches, which offer the best adaptability yet are not the most costly, independent, designed separately, or unmanaged, not contributing any design ( Aaradhanathapliyal, 2019).
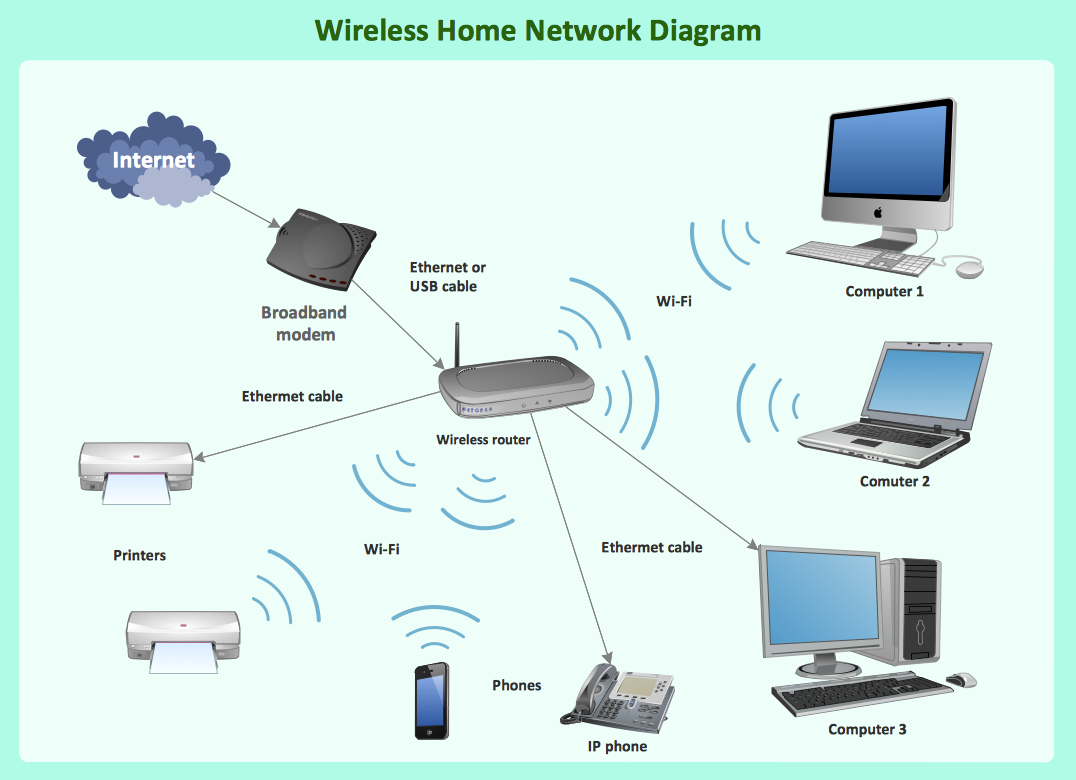
Figure 4
Site 3Beast Technology CompanyChallenges And Implementation
Beast Technology company has been a driving force in the technology realm. Building on another construction, the need to have admission and office processors run efficiently is as vibrant as using state-of-art mainframe laboratories. This suggestion will stay in-line with Beast Technology company mission to take technology and to learn together for a healthier experience for both students and faculty.
The Topology of the Network
The capacity to approach data rapidly will be significant for learners and the staff, also subsequently enhancing the profitability of all. I’m giving this proposition to convey a strong network foundation dependent on Best Technology company’s necessities and new structure. There is an aggregate of a hundred and eighty PCs for learners, the library, and the structural design staff. Notwithstanding the PC, there will be six servers: four for network framework and two for instructional purposes.
Projected Topology
A star topology will be utilized as it is becoming the utmost widely used topology since it is scalable, upsurge performance, and manageable. A star topology is planned where every node is connected unswervingly to a hub, central network hub, or switch. This topology ensures that if a single node (host) flops, it will not distress other nodes linked to the switch (Yadram, 2020). By applying this network framework, all servers’ recited in the network will be improved while lessening the menace of surplus owing to system traffic.
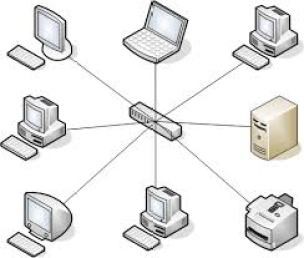
Figure 5 star topology
Organization Media
This organization will be comprised of wired links. This will remove the issues, for example, the impedance that is normal when utilizing wireless networks. Simultaneously impedance is disposed of using the wired networks with more reliable speeds with a few customers on a similar connection. The lone wireless network that will be executed will be for visitor admission. Besides security, another fundamental fear is uptime for the organization and accessibility of quick web browsing for every client. Remote associations, albeit helpful, don’t give the most transient supported network. I will actualize network techniques to accomplish five-nines uptime; this is the most significant uptime level, bringing about 5 minutes each year.
Proposed Network Media
The gear that will be utilized to accomplish the ideal outcomes is recorded underneath:
Network Gadgets
Every PC in the labs, library, and workplaces will be housed on remote connections. I will likewise coordinate a wireless network to permit visitors to interface with the web while utilizing the facilities. There will need five GLS326 connectors, one in every lab, that will associate all hordes and be situated with the worker in their wardrobe. The archive will likewise be utilizing the LGS326 having all hosts associated with the library workforce situated on the staff network. Different workplaces in the structure will be related to a solitary LGS326 switch. The initial and next levels will each house a distant Netgear WNDAP260 Wi-Fi switch.
The gear recorded above is both reasonable and dependable. These controls will give the most significant uptime with simplicity of upkeep. By having the controls situated with workers in every lab, understudies can exploit hands-on labs and work actual investigating situations. The Net stuff switch is a protected choice for permitting visitors to interface with a different network while anywhere nearby without endangering the schools’ network’s security.
Each network should be secure. For the web in the new structure, appropriate security measures should be executed to ensure the understudies, workforce, and the University.
Proposed Security Devices For The Network
A solitary Barracuda NextGen Firewall X100 will join each switch. There will be an aggregate of eight firewalls conveyed. The firewall will fill in as an obstruction, or shield, between your PC organization and web. [3] The design of the structure incorporates servers that will have bolted wardrobes utilizing a fingerprint scanner. I chose the Barracuda NextGen Firewall since it consolidates equipment and programming technology. It will permit the capacity to be managed through their network’s security administration which will upgrade support. The fingerprint device will guarantee approved faculty only can get access to the servers. (Cissco.com)
Computer Systems
The format of the upcoming structure will need a critical measure of equipment. The eight PC labs, six workplaces, and one library will entail hundred and seventy towers, screens, consoles, and mice. Furthermore, there will be an aggregate of six servers, each lab and in every one of the fundamental systems administration storerooms on each ground.
Proposed Processor Structures
The HP Pro Desk G3 400 shall be utilized for having PCs. Each of these frameworks accompanies the latest Windows 10 operating system. Each will have a mouse, console, and an LG 24MC37D screen alongside. The five servers will be the ML350 G9 category of HP ProLiant. I chose the HP Pro Desk PCs since they come pre-introduced with the latest Windows operating system. Once ready for action, every security convention can be hard-pressed to every host. Every one of these frameworks is light-weight and has a little impression. The more significant part of the responsibility will fall on the ProLiant HP servers. Albeit these servers are enormous, they always give versatility, when necessary, later on.
Designing A Network Address
Subnet
The network in the office should be subnetted. Subnetting is the methodology required to segment a solitary physical network into different, more modest sensible sub-networks. ( Shailesh, 2017)
Class Inter-Domain Routing
CIDR or Tactless Inter-Domain Routing displays the number of bits inside an address of a network. I will utilize a default mask of 255.255.255.0 Class C address on account of the organization being executed. The inspiration driving CIDR is to offer a superior adjustment amongst the steering table’s size and effective utilization of the space IP address. The format alongside the prerequisites for every room is explained below.
The structure will line four PC workrooms that will be utilized for guidance. In the structure graphs over, the labs are marked Laboratory #4 and Laboratory #2 on the main floor and Study hall #3 and Laboratory #5 on the subsequent floor; every PC laboratory will have a wardrobe. Every lab will be installed with 30 PCs: 30 understudy PCs, two educator PC, and three servers in the storeroom for storage. Likewise, an Undergraduate PC Lab will give PC admittance to understudies to complete their work. There will be 15 PCs in this lab and a worker in the storeroom. To permit understudies admittance to library assets, the library will likewise have 12 PCs for the overall population to utilize and 3 PCs for library operators. There should be a partition between understudies, staff, and community organizations. The wireless network likewise should be independent of the other trio groups.
At long last, there are different workplaces in the structure. Every one of the workplaces should have two PC for supervisor use, except for the affirmation’s office, with four computers. There are be three worker rooms, one on the main floor, the other on the subsequent floor, and the entrance room to guarantee security, and overall, the University will require progressive observation. A few things will be sent in to help with security checking on the network.
Proposed Measures for Network Security
The Barracuda firewall referenced before has inherent security highlights like an IDS (Interruption Detection System). Interruption identification aims to screen the network’s resources to distinguish abnormal conduct and abuse in the organization. (Jyoti. 2020). will likewise be executing fingerprint scanners on the organization wardrobes to forestall unapproved passage. Every PC will have a security device on them so that inside can’t be messed with. Also, security log conventions will be set up to catch framework logs that are pertinent to security. These conventions will take into account quicker examination and, if there are issues, lead to a quick verdict. The relevant staff should be prepared on specific frameworks relying upon their position’s jobs. All teams and understudies should sign a fair use strategy and see any preparing materials relevant to framework upkeep.
Executing the previously mentioned safety efforts and conventions will guarantee staff, understudies, and the college’s wellbeing. All information for the organization that will be kept up by IT are fundamental and the ISP. They will be conveyed inside a testing climate previously being sent into the creative situation. All vacant open ports should be shut, and the required email ports, web, and application will stay opened and observed. Extra ports can be unlocked upon affirmed demand. Pattern Micro’s X-Generation security will be utilized to protect the network from viruses.
Bibliography
J.R. Simmons 18 Sept 2019, Wired vs. Wireless: A Closer Look
https://www.nojitter.com/enterprise-networking/wired-vs-wireless-closer-look
7 Best Practices of Data Center Cable Management By Herman Chan – 27 JUN, 2019
https://datacenterfrontier.com/data-center-cable-management/
Essential network cabling tips for your infrastructure’, search networking. Techtarget Partsenidis, C. (2017). ‘Essential network cabling tips for your infrastructure,’ searchnetworking.techtarget.com [Online]. Available from: http://searchnetworking.techtarget.com/tutorial/Ten-cabling-tips-in-10-minutes
Yadram On:19th Apr 2020 Types of Network Topology? (2020): |
https://technicalcybersecurity.com/types-of-network-topology/
Aaradhanathapliyal, 09 Aug 2019 Types of switches in Computer Network
https://www.geeksforgeeks.org/types-of-switches-in-computer-network/
2020, What Is a Next-Generation Firewall?
https://www.cisco.com/c/en/us/products/security/firewalls/what-is-a-next-generation-firewall.html
Sisat, Shailesh. (2017). IP Subnetting. International Journal of Knowledge Engineering and Soft Data Paradigms. 2. 5-10.
https://www.researchgate.net/publication/303298395_IP_Subnetting
Snehi, Jyoti. (2020). Review of Existing Datasets for Network Intrusion Detection System.