Essay on Robotic Process Automation
Number of words: 3998
ABSTRACT
RPA, or Robotic Process Automation, is software that replicates a human’s actions when doing repetitive, rule-based tasks. The robot works rapidly and accurately, using the same applications that an organization’s staffs do every day. All activities in conventional automation depend on programming/scripting, APIs, or other integration techniques to back-end systems or internal applications. RPA, on the other hand, automates software that can shift labor from humans to computers, allowing businesses to cease paying people to do work that might be automated and allowing for speedier front and back-office transactions. Robotic process automation (RPA) attracts a lot of corporate attention as part of the ongoing business innovation. While RPA is a hot topic in the business world, most academic research lacks a conceptual and comprehensive study of the topic, creating a slew of problems. Robotic Process Automation (RPA) is the next generation of technology, thus the need for comprehensive research. Robotic Process Automation (RPA) is a cutting-edge technology in the fields of computer science, electronic and telecommunications engineering, mechatronics, and information systems. A combination of software and hardware, social networks, and robotics allows relatively simple tasks to be completed.
Keywords: RPA Software Robots, Intelligent Process Automation, Robots Concept of Bots
CHAPTER 1: RPA TOOLS
Rapise Inflectra
Rapise Inflectra is an RPA tool that serves both ‘Automate Everything and Automation for Everyone.’ It can let you test Everything from the web to smartphones to computers to APIs for’ Automate Everything.’ Rapise is not simply a tester; it is also a thinker. It will also assist you in managing tests that span various technologies at the same time. For ‘Automation for Everyone, anyone can automate with Rapise Inflectra. Rapise keeps track of individuals’ tests and allows them to change them in a simple spreadsheet-based builder. Alternatively, everyone can use their JavaScript-based platform, which is simple to extend (Siderska 47). Rapise can help an individual quickly design the necessary tests. The recording is simple with features like capture once, replay in any website, and live verification during recordings. Test servicing is easy with Rapise, to elements such as scriptless, which make testing human-readable.
There are two operational parameters for Rapise Inflectra: Firstly, there are REST Web Services. It is a built-in specification builder and item library that lets an individual design REST web service queries, analyze the HTTP headers and convert them into a parametric collection of Rapise models in the core Rapise JavaScript interface. Second, there are SOAP Web Services (Siderska 48). It includes a built-in demand tester and object package that lets an individual design SOAP web service calls, examines the returned HTTP headers and SOAP reply content, and then clandestine into a parametric collection of Rapise models be written in the core Rapise JavaScript interface.
Blue Prism
Enterprise difficulties necessitate large-scale automation interventions through Blue Prism. Blue Prism Intelligent automation widens the breadth of a firm’s work. It can automate, enhance efficiencies and ROI, thanks to an intelligent digital staff that gradually handles tasks whenever they want. Blue Prism’s Operational Parameter is Command-line Robotic model. A cloud-first design and delivery philosophy gives an individual the most operational options, improves its connected business, and provides its business users with the quickest and most feasible way to automate (Hofmann, Samp, and Urbach 101). Blue Prism’s innovative security workers are well-organized, multitasking robotic arms that automate corporate activities using a company’s existing systems, equipment, and solutions.
UiPath
UiPath speeds up and lowers the cost of digitalization by streamlining processes, identifying efficiencies, and providing insights. It makes use of current systems to reduce downtime. A firm’s teams will spend more time on work to yield more significant results by automated processes. The Marketplace’s upwards of 200 ready-made parts give your staff more time—in less timeframe. The operational parameters are BOTs from UiPath, which boost conformity by executing the exact procedure that satisfies your requirements. Reporting keeps track of your robots so that you may access the documentation at any time (Hofmann, Samp, and Urbach 104). Staff is free to provide extra support to a firm’s highest-level consumers when robots do jobs, resulting in more efficient improvement and development.
Automate Anywhere
The Automate Anywhere site is robust enough to automate processes of any sophistication while still being simple enough to use by anybody on your team. The Automation Anywhere solutions team has helped businesses of all sizes digitize their business operations, identify new automation concepts, and maximize their return on investment. ‘Automate Anywhere’ enables people whose thoughts, thoughts, and focus contribute to the success of the businesses for which they work (Hofmann, Samp, and Urbach 105). The operational parameters and Developer Portal, A-People Community, and Community Edition. They provide the most advanced Digital Workforce Network around the globe, making the job more natural by automating corporate processes and freeing people.
CHAPTER 2: HISTORY OF APPLIED USES OF RPA TECHNOLOGY
Automated Manufacturing (1970 to 90)
We observed the computerization of business areas in many corporations during the early stages of the Tech Revolution. Data Warehouses, or MIS, groups inside each company were in charge of this (Agostinelli et al. 26). Quality management (TQM) and chronological process quality improvement methodologies were used in this stage of process advancement.
Management of Business Processes (90+)
BPM (Business Process Management) is a technique for optimizing end-to-end business operations. As the computer giants of the 1990s (such as IBM and Java) jumped on board, they drew with them a slew of automated robotic technology.
(2000+) RPA
RPA first appeared in the 2000s, with Blue Prism releasing their initial solution in 2003, followed by UiPath and Automation Anywhere, both of which were formed simultaneously. “We started focused on the BPO industry as a path to market,” says Alastair Bathgate, Executive Director of Blue prism. UiPath’s solution has also begun to gain momentum with an Indian Service firm (Ribeiro et al. 53) RPA began as a technique to cut costs in BPO and has since expanded to include Shared Services, IT leasing, and other transaction sectors. Outsourcing lowers costs by transferring lower-level manual jobs and procedures to less expensive labor. They were examining several levers to keep delivering annual cost reductions to their clients. RPA began by enhancing the monotonous operations carried out by these Service providers to continue to minimize costs.
The top three RPA tools have a long history
The employment of numerous technologies to tackle business issues has led to RPA. It began with simple legacy technologies such as screen scraping in conjunction with Automation processing software. The cognitive components of RPA technologies have begun to appear with the introduction of Artificial Intelligence.
Blue Prism: Blue Prism was founded to provide BPOs with an “external provider of the workforce.” They profess to be the first to coin the phrase “RPA.” “We were conducting RPA procedure before it was named robotic process automation,” says Bathgate, the RPA tools director. From the start, Blue Prism was focused on building a Digital workforce, and they were thinking about how to solve the challenge of performing things that an outsourced robot would do, such as executing the work and scheduling them (Beerbaum 68). As a result, it is constructed within that. To design the activities to be completed by the Bot, they use a Ms. Visio-like layout. Using a management console, these Bots may then be launched and controlled.
UiPath: It began by developing automation tools and application programming interfaces (formerly known as DeskOver). IBM, eBay, and Qualcomm were among the firms that used these automated libraries. A few of their goods still include these libraries. UiPath then appears to have started to commercialize these libraries (Beerbaum 73). Their product didn’t get much momentum at first. They were identified by an Indian BPO business conducting a pilot study to determine the top vendor of RPA tech machines.
Anywhere Automation: Gondwana Solutions, the forerunner of ‘Automation Anywhere,’ was created in 2003. Tethys is named after the Greek divinity god of water. Their goal was to make system integration as common as drinking water. They have a great vision, and they appear to be achieving it to a large extent.
RPA Trends for the Future
RPA is part of what Everest refers to as a feedback loop, in which actual worth leads to additional capital being put in tools that provide more and more value. We should expect RPA tools to improve and add additional functionality as a result of the enormous investment. RPA is being adopted and implemented by an increasing number of businesses. AI is becoming a part of RPA. Unorganized data analysis, prescriptive analytics insights, and basic judgment-based robotics are all RPA tools we may expect to see shortly (Bakarich and O’Brien 39). One of the most challenging aspects of implementing RPA is identifying, shortlisting, and prioritizing suitable activities for robotics.
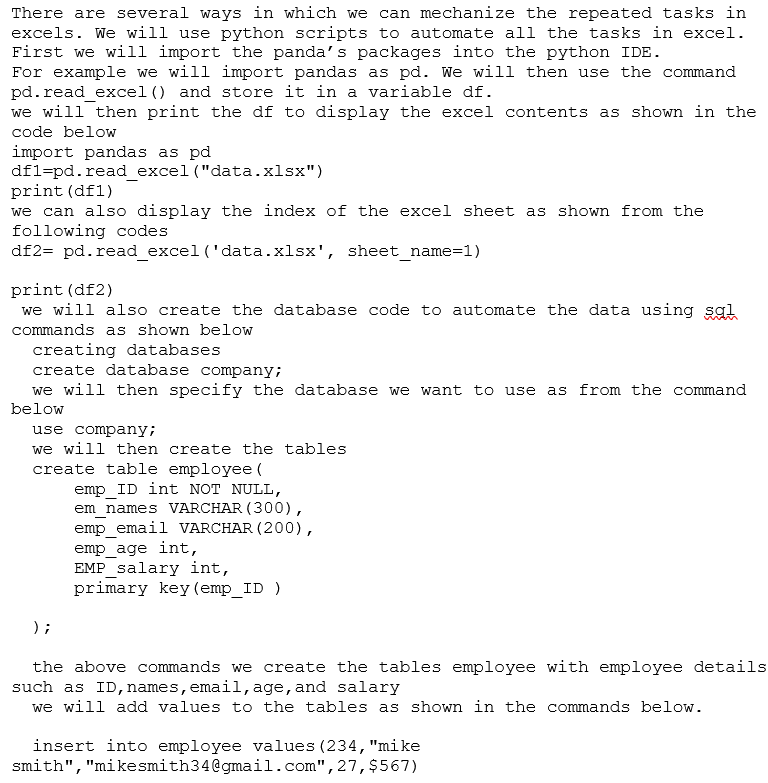
CHAPTER 5: CASE STUDY
The improved technology has led to Robot process automation (RPA), which led to business process execution such as faster and efficient resource planning, customer relationship management, and payroll system. The Robot process automation was developed to help with office tasks. The hackers use denial of service attacks to interfere with the host machines; thus, the host cannot respond to any request being made by the trusted pair in a communication channel. The denial of service attack most affects the network architecture, system server architecture, and software architecture. Downloaded bugs in the computer system resulting from operating system updates may make the computer system vulnerable to denial and service attackers. In addition to that, the denial of service attack may also come as a result of the company system administrator acknowledging and allowing the attack to take place or the hacker sending the network host machine more packets than what the host machine can process, making the host system busy and preventing it from receiving more packets from its trusted pair. It makes the system consume a lot of bandwidth and computer resources. The denial of service attack can be remedied by using network address translation to prevent network traffic from coming from particular network addresses or ports. We can also use the filters in the router to prevent denial of service attacks (Ericsson 1504).
The corporation or business identifies the cyber intrusion through the following: first by identifying mysterious emails. The hacker uses phishing attacks to gain access to sensitive business information pretending to be genuine and trusted. Therefore, company employees are needed to practice safe email protocols and avoid clicking on links from unknown sources or downloading and opening emails documents. The employees must not reply to those emails as it could lead to the recipient’s email validation hence continued attacks. Secondly, by noting unusual password activities, for example, the employee being signed out of the system and notifying them that their email password has been changed. That could be the possibility that the user’s password has been compromised, and immediate action is needed. The employees must create a strong password for the system and email, which should be updated every six months. In addition to that, we also have to identify suspicious pop-ups or adverts as another point. The employees are required not to click on the unknown pop-ups as most of them are infected with viruses, compromising the system networks. The business administrator’s response to the cyber intrusion includes the following.
First and foremost, we have to ensure that all the system software is kept up-to-date to help to protect the system from malware attacks. In addition to that, the employees must create a strong password for system and email, which should be updated every six months. Then last, but not least is that the Company employees are therefore needed to practice safe email protocols and avoid clicking on links from unknown sources or downloading and opening emails documents. The employees must not reply to those emails as it could lead to the recipient’s email validation hence continued attacks.
CHAPTER 6: RPA SECURITY
The RPA new digital workforce requires special access and permissions to interact with target systems and several other applications, including financial systems, ERP, CRM, supply chain and logistics systems, or even email to conduct automated functional activities (Lacity, Mary, and Willcocks 78). Such privileged identities can be exposed to targeted, accreditation cyber assaults if they are left unprotected. Because robots may be manufactured automatically, the number of connected devices installed within a company can quickly rise. As a result, such a number may need to vary regularly, increasing security issues (Lacity, Mary, and Willcocks 78). If sensitive account credentials used by robot scripts are kept unsafely, they can drastically increase the attack surface. If firms use standard credentials to install Remote Desktop Applications (RDA) robots, sometimes known as “unattended RPA,” the hazards are considerably higher. Currently, Organizations are looking for solutions to link automation with effective privacy measures that can help secure RPA resources while also acknowledging faster time to value as RPA implementations rise and the number of software robots grows.
Protecting sensitive information and access for software robots should adhere to similar security requirements as humans and programs, such as the least privileged approach. There are, however, a few operational adjustments particular to RPA technology and the robot lifetime that must be made. For instance, there is a need to eliminate hard-coded identities from robot interface scripts to increase RPA security (Lacity, Mary, and Willcocks 78). While RPA technology is still in its infancy in terms of how it will alter enterprises, most technologies have the potential to increase the attack surface if not used appropriately. However, CyberArk can assist in the privacy management of sensitive account information used in RPA technologies and software robot implementations. In most cases, CyberArk communicates with a broad range of RPA solutions than any privileged access management (PAM) provider on the field.
CHAPTER 7: RPA SECURITY RISKS AND CHALLENGES
Both RPA software and RPA deployments add to the threat landscape. Given the fast use of robotics and automation, it becomes easy to forecast that it will become a substantial source of risk for business (Syed et al. 103162). As a result, this situation may lead to a rise in demand for weaknesses in the future. Another area under consideration is password security for software robots. For example, suppose password security is not adequately maintained in accordance with an organization’s policy requirements (Syed et al. 103162). In that case, such a shortcoming might lead to internal deception and enable intruders to launch assaults across a wide range of procedures once they have gained access to the network. Relatively, before completing their tasks, RPA software robots need access to specific systems and resources. They might well be logging into ERP or CRM systems, or they could be included in a workflow using RPA and AI. The bot will be coded to acquire access and carry out its activities. Because of this, RPAs are vulnerable to hackers attempting to recover identities or passwords.
Software robots may become vulnerable for business operations in terms of productivity or finances once they are implemented. For instance, when a strategic planning process does not adequately protect a company’s RPA, a single technology robot’s malfunction might result in a disaster (Heinzl et al. 270). In most cases, there is often a need to include software robots in the change management process as a different investment portfolio. The failure to meet such requirements, combined with the lack of specified dependencies on other software components, might result in service outages or processing issues. It is considerably more challenging with cognitive RPAs, which demand a unique approach to change management like any other machine-learning algorithm (Heinzl et al. 270). Relatively, Self-inflicted code and algorithm changes brought on by the processing of fresh data sets provide another point of failure.
Most companies nowadays struggle to adequately uncover their assets due to a lack of resources. Furthermore, numerous legacy apps are difficult to manage, maintain, and safeguard (Heinzl et al. 270). RPAs are designed in such a way that even non-IT individuals can create them. As such, Organisations may be faced with a large number of software robots developed in a short amount of time if no controls are placed around the technology, offering significant operational dangers.
CHAPTER 8: RPA SECURITY BEST PRACTICES
Security reporting quality, consistency, and efficiency can all be improved with robotics. Automated, regular security posture assessment, for example, can be put into a robotics-driven, complete reporting process, which provides managers with summaries of identified points of contention (Matthews, Peter, and Greenspan 73). RPA can aid in automated testing within the context of information security. Robotics, for example, might make conformity testing to policy for privacy settings on servers, routers, modems, and apps better and more accurately. Periodic tests could be carried out and the results put into computerized dashboards.
In business, robotics can be used to automate exploration and management applications. Once found, cognitive learning can be utilized to automate the application’s risk level based on the data and controls found (Egiyi et al 44). Bots can also be used to identify and modify inventory and control mechanisms continually. In the software development life cycle, cognitive learning can be utilized to perform gate checks for security activities (SDLC). Bots can gather data from project management tools or automated systems to determine when a codebase is ready to move onto another phase of the SDLC (Egiyi et al 44). To determine whether a vulnerability debt on an application should be remediated, algorithms can be created and supplied into automated reports for dashboarding.
Robotics can be deployed to generate automated information about URLs and code that need to be evaluated to do a thorough vulnerability analysis of the apps. Bots can help with the effective scalability of several apps simultaneously and triage newly discovered risks (Geetha, Malini, and Indhumathi 5). The outcomes of the assessments can also be incorporated with standard developer portals for cognitive training bot remediation. Through the automation of the majority of de-provisioning/provisioning procedures, robotics can assist reduce reliance on big help desk and operations personnel. When compared to manual processing, it may result in an 8x improvement in computerized request fulfillment periods.
Robotics can assist managers in focusing on more critical access concerns during the review process by increasing the efficiency and quality of access data validation. If any abnormalities are identified while completing data validations, it can be trained to construct and deliver confirmation signals to users (Geetha, Malini, and Indhumathi 5). Robotics can help analyze corporate vulnerabilities and prioritize repair efforts, improving the efficiency and quality of the vulnerability and risk program. It can then be used to alert management and process administrators of the remediation operations and conduct verification to monitor conformance.
CHAPTER 9: LITERATURE SURVEY ABOUT CYBERSECURITY CONCEPTS AND LAW ENFORCEMENT
Most organizations in the world now face cybersecurity challenges in that about 79% of the company shows that the top five business risks are cybersecurity. According to the research study conducted by the KPMG, the cybersecurity risks have increased from 41% to 59%, which makes the cyber-security day by day boardroom agenda. In addition to that, the malware attacks were recorded the highest percentage amongst the problem being faced by cyber-attacks in an organization with 73%, followed by phishing with 49%. Around 43% of the cooperates have experienced ransomware attacks in the past years. As opposed to the business views recorded, it’s believed that only 73% of the law enforcement authorities ATM theft becomes the most commonly reported crime followed by phishing attacks with 46.9% and data theft with around 39.9%. 46% of the business cooperates are not prepared to handle the ransomware attack as a significant cyber-attack (Yan 2012).
However, according to the law enforcement authorities, more than 50% of cyber-security cases are being reported each year. The primary concern being the availability of information and awareness in that 35% of the company shows that cyber-security information is through prevention, reporting the incidents, and investigation. From our study also 30% of the companies have well-defined planning and requirements regarding cyber-security attacks and prevention.
In addition to that, only 80% of the companies have adopted the new technologies. These new technologies include social media, cloud computing, mobility, and digital enhancement. It indicates that most companies have cyber-security budgets to help to safeguard their gadgets from cyber-attacks. There has been an increase in attention on cyber-attacks as from the research study conducted. The audit committees provided it.
CONCLUSION
In conclusion, RPA, the much-hyped technique that automates regular digital operations previously performed by people, has a lengthy history, extending back to the 1950s with the advent of macros. The phrase itself, as well as the core technology that underpin contemporary devices, are relatively new. Here’s a timeline of RPA’s development. There were numerous forerunners to contemporary RPA solutions. Banks began creating data-scraping programs in the early 1980s to grab data from different financial information services such as Reuters and Quotron. Later, several manufacturers began developing more advanced solutions for cutting and pasting data from classic terminal apps to more current web services. Because automation as a concept has been the underlying narrative of IT for years, the actual evolution of RPA is challenging to pin down. RPA occurred in 3 waves: Various types of programmable automation tools, such as Excel macros, were included in the initial wave. The second wave arose from test automation technologies pioneered by businesses such as OpenSpan, which Pegasystems later bought, the BPM solutions behemoth. The creation of enterprise-grade automation technology with complete governance and security integrated into Blue Prism: one of the “three largest” RPA vendors and Automate Anywhere and UiPath, started off the current wave.
Works Cited
Agostinelli, Simone, et al. “Automated generation of executable RPA scripts from user interface logs.” International Conference on Business Process Management. Springer, Cham, 2020.
Bakarich, Kathleen M., and Patrick E. O’Brien. “The robots are coming… but aren’t here yet: The use of artificial intelligence technologies in the public accounting profession.” Journal of Emerging Technologies in Accounting 18.1 (2021): 27-43.
Beerbaum, Dirk. “Artificial Intelligence Ethics Taxonomy-Robotic Process Automation (RPA) as a business case.” Artificial Intelligence Ethics Taxonomy-Robotic Process Automation (RPA) as Business Case (April 26, 2021). Special Issue ‘Artificial Intelligence& Ethics’ European Scientific Journal (2021).
Egiyi, Modesta Amaka, and Victoria Nnenna PhD Chukwuani. “Robotic Process Automation (RPA): Its Application and the Place for Accountants in the 21st Century.”
Ericsson, G. N. “Cybersecurity and power system communication.” essential parts of smart grid infrastructure. Power Delivery, (2010): 1501-1507. IEEE Transactions.
Geetha, T., A. Malini, and M. Indhumathi. “Robotic Process Automation.” Int J Comput Techniques 7.5 (2020): 1-12.
Hofmann, Peter, Caroline Samp, and Nils Urbach. “Robotic process automation.” Electronic Markets 30.1 (2020): 99-106.
Lacity, Mary, and Leslie P. Willcocks. Robotic process automation and risk mitigation: The definitive guide. SB Publishing, 2017.
Matthews, Peter, and Steven Greenspan. “Robotic Process Automation.” Automation and Collaborative Robotics. Apress, Berkeley, CA, 2020. 71-107.
Ribeiro, Jorge, et al. “Robotic Process Automation and Artificial Intelligence in Industry 4.0–A Literature review.” Procedia Computer Science 181 (2021): 51-58.
Siderska, Julia. “Robotic Process Automation—a driver of digital transformation?” Engineering Management in Production and Services 12.2 (2020).
Syed, Rehan, Suriadi Suriadi, Michael Adams, Wasana Bandara, Sander JJ Leemans, Chun Ouyang, Arthur HM ter Hofstede, Inge van de Weerd, Moe Thandar Wynn, and Hajo A. Reijers. “Robotic process automation: contemporary themes and challenges.” Computers in Industry 115 (2020): 103162.
Van der Aalst, Wil MP, Martin Bichler, and Armin Heinzl. “Robotic process automation.” (2018): 269-272.
Yan, Y., Qian, Y., Sharif, H., & Tipper, D. (2012). A survey on cybersecurity for innovative grid communications. Communications Surveys & Tutorials, IEEE, 14(4), 998-1010.