Essay on Current Development in Software Security
Number of words: 2420
Abstract
Software security is most efficient if prearranged and managed in every phase of software development life cycle, particularly in precarious presentations or those that possess sensitive data. The resolution to software security advancement is more than technology enhancement only. Due to the improvement in technology, software security threats have equally increased. Consequently, more priority has been directed to software security, encouraging more excellent progress in software security to deal with the imminent dangers. This paper, through a detailed review of the works of literature, presents the current developments in software security regarding the malware detection, software process maturity, and runtime software controls, as well the disadvantages and advantages that faces the software safety in the contemporary world.
Introduction
Software security is a concept executed to safeguard software against malicious attack and other hacker menaces so that the software remains to function properly under such possible dangers [1]. Security is required to provide integrity, authentication, and accessibility. Security software is a common expression used to describe any software that ensures that a computer or network is safe from external threats. Therefore, software security engineer should be able to look at the incidence in a security perspective so that security issues can be foreseen. There are various categories of security and privacy software such as access control, anti-malware, anti-key-loggers, anti-spyware, anti-subversion, anti-tamper, cryptographic, and anti-virus software [1]. The misconfigured software, unpatched operating systems, and insecure computer activities all result in generating computer security risks. Computers usually encounter security risks from the following threats: privilege escalation, virus, worm, Trojan, spyware, spam, adware, and rootkits [1]. The security of a computer is essential, mainly to protect information from any threats. Besides, computer security provides general well-being of computers by preventing viruses and malware from attacking them and enabling computer programs to run more efficiently.
In this regard, the cyber-security community, over the past years, has been very vocal about discovering various approaches of improving software since most susceptibilities consist of compatible defects introduced through poorly transcribed code [2]. The modern researchers in the field of cyber-security have discovered that software security has made substantial advancements, as well as pointing out areas for future developments in safe application delivery. Regrettably, rushing to current DevOps coding and high demands of software advertising have overshadowed several perfection concerns [2]. As an alternative, the cyber-security community has broadly embraced a strategy that minimizes cybersecurity threats in software through the application of appropriate procedures, tools, methods, and techniques, each dealing with a particular feature of the risk consequences of bad coding [2]. This paper, through a detailed review of the works of literature, surveys current development in each component of this joint strategy, together with the advantages and disadvantages of minimizing cybersecurity threats.
Advanced Malware Detection
Despite the fact that software security remains to be influenced by advanced programming techniques, the primary focus of the cyber-security community is on malware detection [3]. Even though everyone expects to circumvent or avert exploitable viruses, there is an agreement that it is fundamentally impossible for non-trivial code. Therefore, vendors have created trivial empires based on the presumed right postulation. The methods of detecting malware in a system are classified as illustrated in the figure below [4].
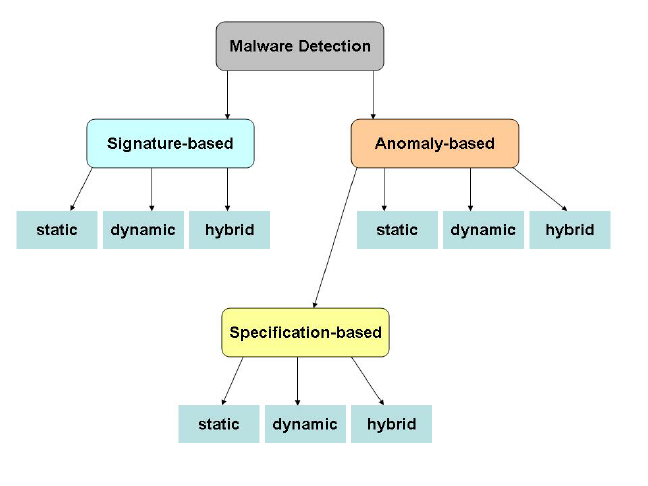
Classification of Malware Detection
However, the original techniques of detecting malware were created on the corresponding application code to signatures, current approaches of analyzing characteristics for indication of objectionable runtime activity [2]. The behavioral investigation is allowed through the dynamic provision of cybernetic equipment for secure setting off of operations that can be executed. In the absence of such cybernetic settings, the behavioral review would be very unsafe for production systems [5].
Currently, most researches concerning malware detection employ machine learning to assist in training security methods of identifying lousy code from models. Profound learning procedures apply substantial parallelism to enhance such kinds of efficiencies of algorithms. Moreover, maybe the unifying factor of this developing sector is that malware detection techniques assume the continuous presence of complications, which assists in justifying business venture through start-ups and other software security retailers [5].
Remarkably, the possibility for the software experts to improve their knack to the point of the complete non-existence of the malware is extremely low. Perhaps this scenario may exist due to innovative malware circumvention techniques. For years, advanced malware protection has depended on malware sandbox to prevent the distribution of malicious documents. However, the sophisticated malware circumvents being detected by sandboxes or other software security control systems by modifying its character and embracing various evasion approaches such as [6]:
- Stalling delays: the malware merely does not perform anything for a long-drawn-out duration. Typically, approximately about 10 minutes is enough for most sandboxes to time-out and presume the object is non-threatening.
- User action needed: the malware does nothing malicious until the user carries out a particular activity, for instance, opening or closing a file.
- Suspended activities: the malware typically suspends any malicious action when it operates within a sandbox. Therefore, it can only inject and modify the code within other applications, develop tenacity, download additional code, move crosswise the network, and connect to its C & C servers.
- Fragmentation: the malware divides itself into several fragments that merely perform when they are rejoined.
- The return-oriented programming (ROP) evasion: the malware inserts functionality into another procedure deprived of the code modification of that procedure. This process is realized through the adjustment of the stack’s contents, which is the set of memory addresses that direct the system to the section of the code to be executed afterward.
- Rootkits: the malware puts the malicious code in a hideout in the lower strata of the operating system where the conventional sandbox tools cannot perceive it.
- Another modern development in malware detection evasion is the establishment of a file-less malware that does not exist in a file. These threats remain residing exclusively in memory and concealed from most innovative malware detection implements, making it exceedingly challenging to discover.
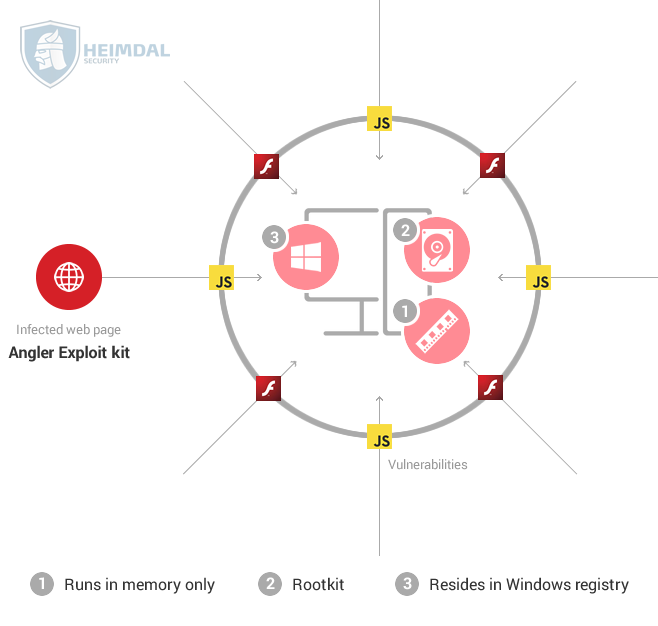
A File-less Malware
Therefore, industries that deal with the detection and control of malware should anticipate a sustained vitality of their combined provisions regarding revenue, sales, and growth.
Software Process Maturity
Software process maturity occurs in five levels: the initial stage, the repeatable phase, the defined level, the managed phase, and the optimizing stage as illustrated below
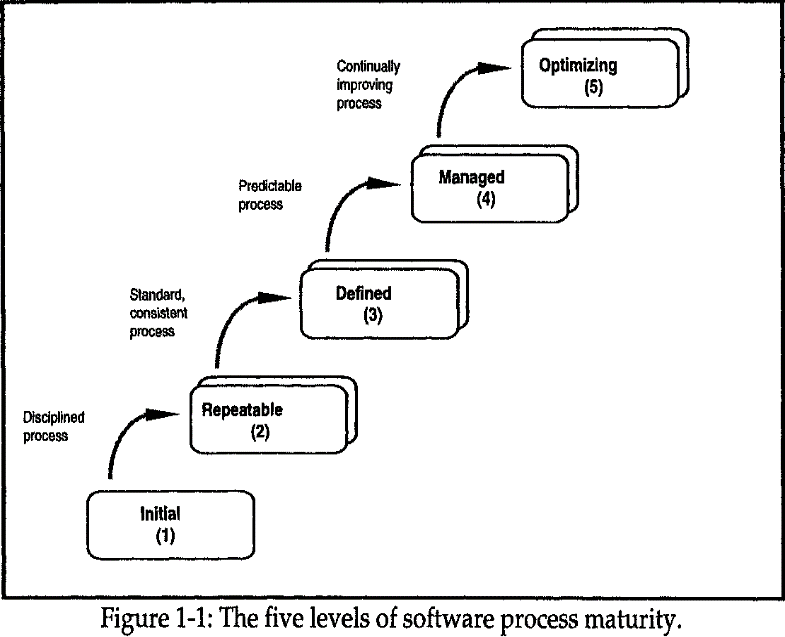
Levels of software process maturity.
The contemporary software security also focuses on conjecturing code security through its related software procedure [3]. Explicitly, numerous software security professionals have postulated that, instead of directly scrutinizing software for the presence of malware or susceptibilities, the development progress of the software should be examined. The theory backing up this technique is mainly experimental; that good code typically originates from well-trained designers who work with topnotch equipment in the contemporary and active development settings [2]. However, exploitable susceptibilities, in most cases, have been discovered in code inscribed by poorly trained designers applying ad hoc equipment in off-the-cuff development settings.
Therefore, software maturity models have developed to associate the level of software security to the quality of the procedure. This process has the necessary side effect of pushing for the advanced safety of all code that develops from a particular software procedure of the vendor [5]. Some of the techniques required in such systems are periodic penetration testing, automation, and maintenance processes. The process maturity is beneficial since there is a small downside in every attempt to enhance the procedures of creating code. Moreover, advanced software security procedures result in code saving, time-to-market enhancements, and high quality [2].
Review and Scanning of the Software
There are two types of scanning techniques: passive and active. The vulnerability assessment is often carried out mainly to discover threats through the application of automated testing tools such as network security scanners [4]. Moreover, vulnerability scanning is a computer safety method that identifies faults in a cyber-security system. The following are the types of vulnerability scanners: Network enumerator, port scanner, network vulnerability scanner, web application security scanner, and computer worm [6].
Conversely, a review is a systematic examination of a document by the programmers with the primary objective of discovering and eliminating faults in the software expansion life cycle [2]. Reviews, in most cases, validate documents such as requests, structure design, code, experiment cases, and assessment strategies. The security code review is mostly embraced to audit the source of code so that an application can substantiate that appropriate security controls are available, and they function effectively [5]. Besides, software reliability is an essential aspect impacting on the system reliability, and its measurement is still in its early stages of development [5].
The examination of code and the application of code-scanning techniques are the conventional ways of enhancing software security. In 1970 at Bell Labs, the tools that were used were able to scan C code and recommend enhancements [2]. Consequently, all resulting code-scanning technology seemed to trace their origin to this early theory.
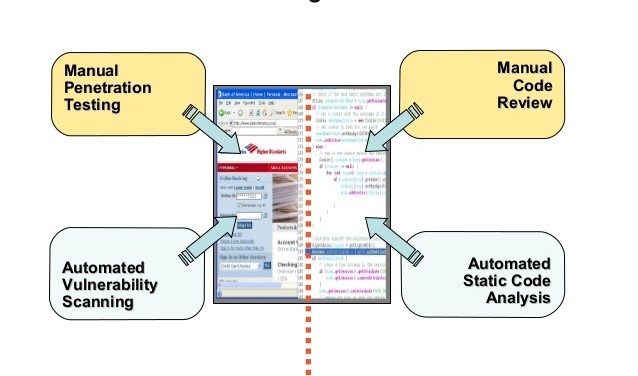
Code Scanning
The software security community debates on the current application of the manual code assessments while traditionalists insist that human review is vital in maintaining high quality and securing items [2]. The conventional perspective is being challenged with the rapid cycle times in the DevOps setting where limited time is available for human inspection. The modern technique to be adopted in such an environment is automated scans. Therefore, current DevOps and cloud-based software development settings are suitable environments for standard and well-evaluated modules [5].
Runtime Software Controls
The current runtime software controls require dynamic update since they embrace make-shift techniques. These systems can be improved through the application of a systematic and principled method to runtime modification backed up by an exploitable infrastructure [6]. The advantages of runtime advancements are not limited to security-intensive. However, modern commercial software experiences the same characteristics in an attempt to offer end-user customizability and extensibility [4]. Recently, runtime extension features have developed to readily accessible in standard operating systems.
The runtime facilities that exist in the modern operating systems programming languages have several drawbacks. The primary shortcoming of these facilities is that they do not guarantee the dependability, constancy, accuracy, or the anticipated features of runtime variation [6]. The change management is very crucial to utilize instruments for runtime change efficiently. Change management is an essential feature of runtime system growth that assists in identifying things that should be modified [4]. It also provides an environment for deliberating about, stipulating, and executing change. Therefore, in the absence of change management, the dangers presented by the runtime changes may be more than those attributed to shutting down or restarting the system.
The application of runtime controls that are rooted in the implementation settings is the most promising improvement in software security. This method is also referred to as runtime application self-protection (RASP). A programmed safety setting, one that covers for code vulnerabilities, is created through the incorporation of behavioral and machine-learning within processes that can be executed [4]. Besides, several software advancement organizations embrace the application of RASP controls, DevOps, and cloud enhancement primarily to improve conveyed speed and flexibility of the code. RASP minimizes the threats of any form. For instance, the SMOTION runtime software can be customized to perform the desired task.
The SMOTION Runtime Software
Similarly, machine-learning methods have developed to the extent that the experimental behaviors can act as training data to tag innovative variations of software achievements [5]. Deep-learning advancements are also promising developments in software security. This advancement is due to the enhanced effectiveness and monumental parallelism which are associated with the technique. Besides, the approach is flawlessly well-matched to the numerous integrations that have to be inspected in a standard software implementation [5].
General Advantages and Disadvantages of Software Security in the Contemporary world
There are various benefits of cyber-security in the modern eras that push for its adoption. First, it safeguards the current computer systems against worms, viruses, spyware, and any other malicious programs [1]. It also provides fortification against data pilferages. Moreover, software security provides a close-fitting environment that hackers find it extremely difficult to carry out their malicious actions. It also minimizes freezing and crashing of the computer, as well as ensuring privacy to the users [6].
On the other hand, cyber-security has some drawbacks that impede its application. First, the correct configuration of firewalls sometimes proves to be very challenging to the developers [1]. Consequently, an incorrect setting of firewalls may ultimately inhibit users from carrying out particular activities on the internet. Moreover, it makes the whole system to function at a slower rate than before [1]. Therefore, the new software needs to be updated periodically to maintain security status up-to-date. Finally, the cost of purchasing the software might be expensive for a regular user with average financial capacity [6].
Conclusion
In summary, the primary emphasis on the methodology is an essential consideration in ensuring the safety of the software. Nonetheless, the cyber-security community has embraced various applicable procedures to enhance the quality of the code and ensure safety in the absence of any actual right improvement by program experts. Software security professionals should be realistic in their effort of minimizing software threats. Besides, with the contemporary infrastructure’s dependency on well-fashioned code with the least possible vulnerable faults, there is an anticipation of synthesized techniques with advanced programming languages and continuous improvement in programming technology that minimizes risk [5]. Finally, this paper presents the current advances in software security regarding the malware detection, software process maturity, and runtime software controls, as well the disadvantages and advantages that faces the software safety in the contemporary world.
References
H. Fujita, New trends in software methodologies, tools, and techniques., Amsterdam: IOS Press, 2010.
D. Ashbaugh, Security software development, Boca Raton: CRC Press, 2009.
J. Vacca, Managing information security, Amsterdam: Syngress, 2014.
E. Amoroso, “Recent Progress in Software Security,” IEEE Software, vol. 35, no. 2, pp. 11-13, 2018.
Chou and C. Fan, “Regulatory-based development processes for software security in nuclear safety systems,” Progress in Nuclear Energy, vol. 52, no. 4, pp. 395-402, 2010.
B. Potter, “Software & network security,” Network Security, vol. 2004, no. 10, pp. 4-5, 2004.